When the application uses GAMRemote Authentication Type for implementing SSO, several calls are made between the client and the Identity Provider (from now on, the server).
This article explains the steps performed by GeneXus Access Manager (GAM) when SSO is used for authentication.
Suppose that Login Object for Web property = GAMSSOLogin at the client KB.
When a private object is executed, the flow is automatically driven to the GAMSSOLogin object. If there isn't a valid local session for the user, the GAMRepository.LoginGAMRemote() method is executed. This behavior triggers a sequence of calls that follow the OAuth 2.0 protocol.
Here's a scenario describing the flow. Consider that webpanel1 is a private object, and there isn't a valid session to execute it.
1. As webpanel1 is a private object and Login Object for Web property = GAMSSOLogin, a redirect to GAMSSOLogin is performed.
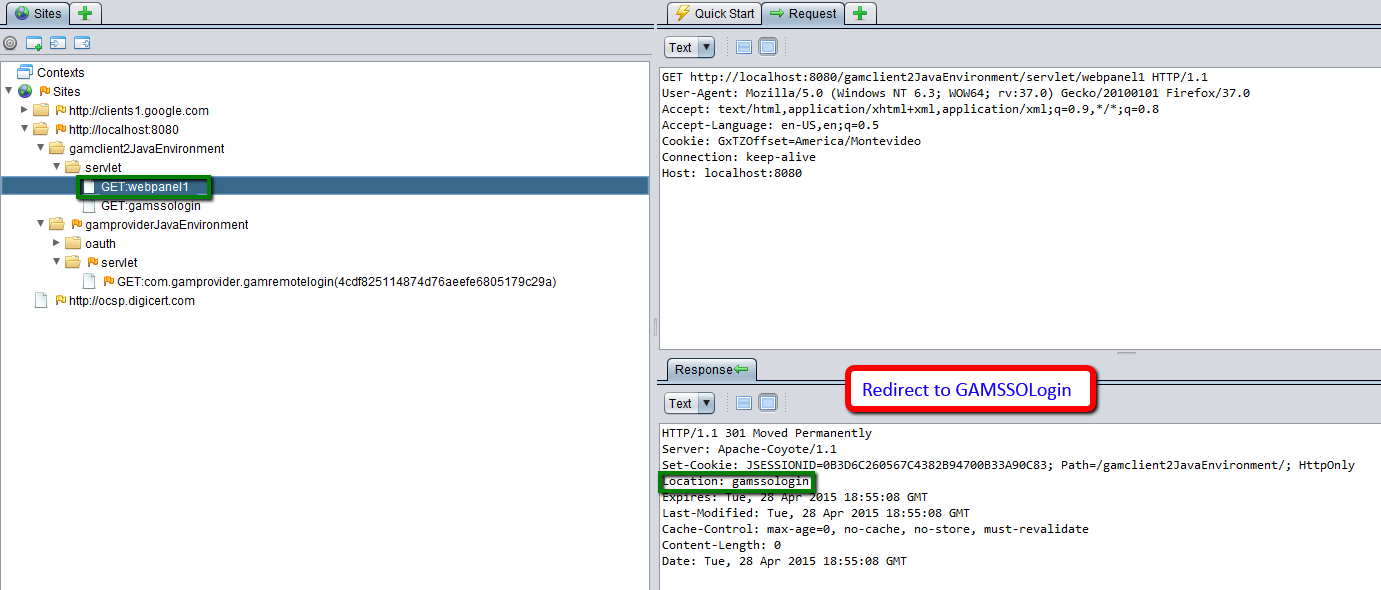
2. The GAMSSOLogin object checks if there is a valid session, and if there isn't one- a security exception occurs - it calls the GAMRepository.LoginGAMRemote() method. This method executes a redirect to the server with the following format:
oauth/gam/signin?oauth=auth&client_id=....&redirect_uri=....&scope=.....&state=....
where
- client_id is the Client Id of the GAM Application defined on the client.
- redirect_uri is ../oauth/gam/callback.
- scope can be: gam_user_data, gam_user_roles, gam_user_additional_data (any or all of them, separated by '+')
- The state is a random string
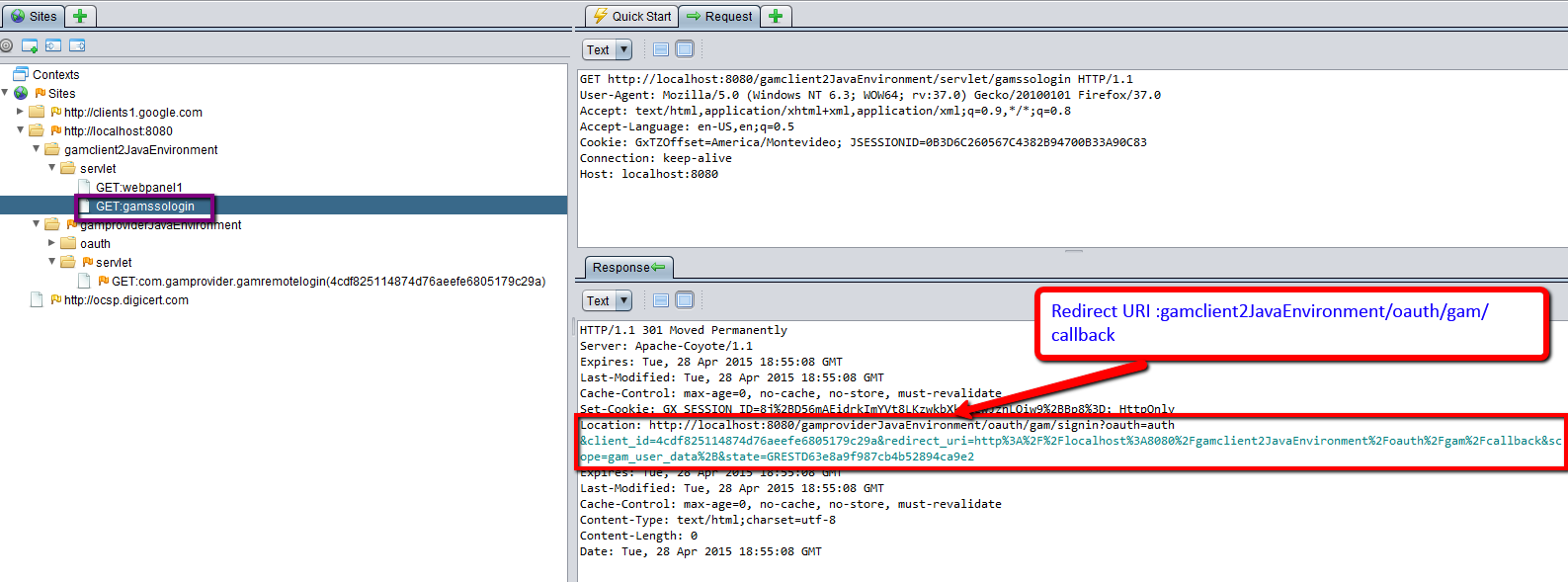
3. The response to the previous execution is a redirect to GAMRemoteLogin object if there isn't a valid session on the server.
Note: The GAMRemoteLogin object is any object configured in the Local Login URL of the Identity Provider configuration.
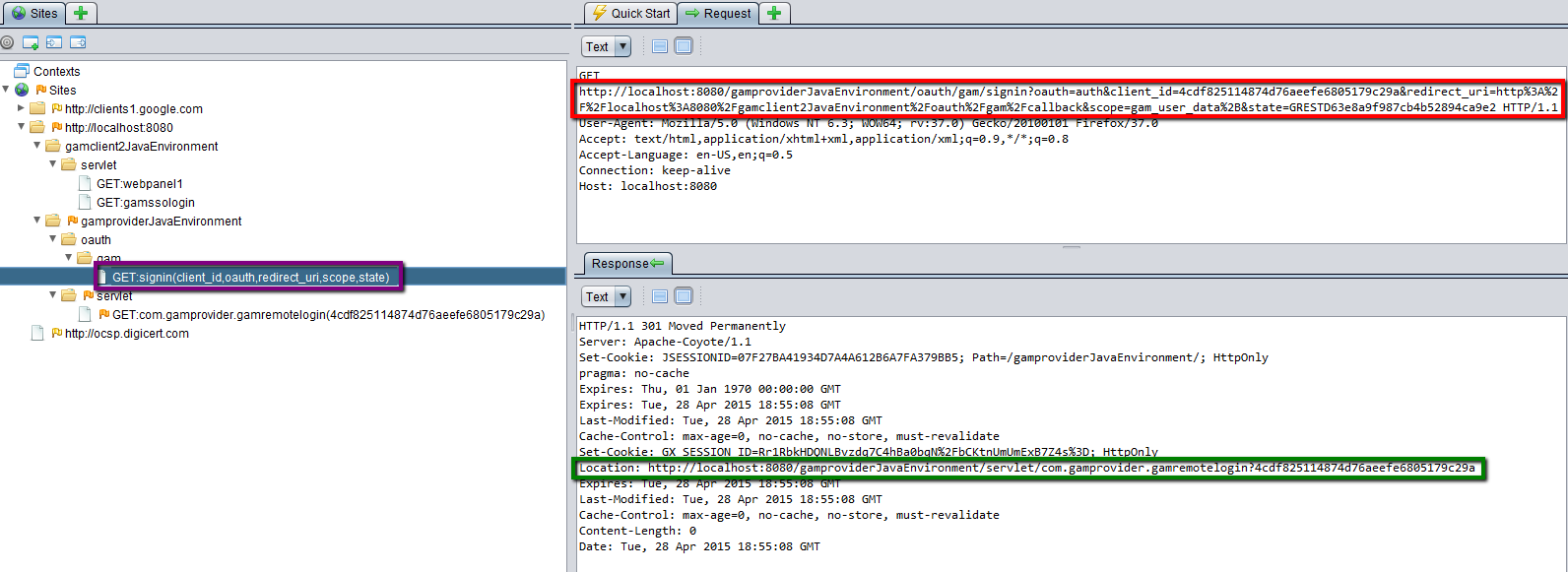
4. The GAMRemoteLogin object is executed on the server.
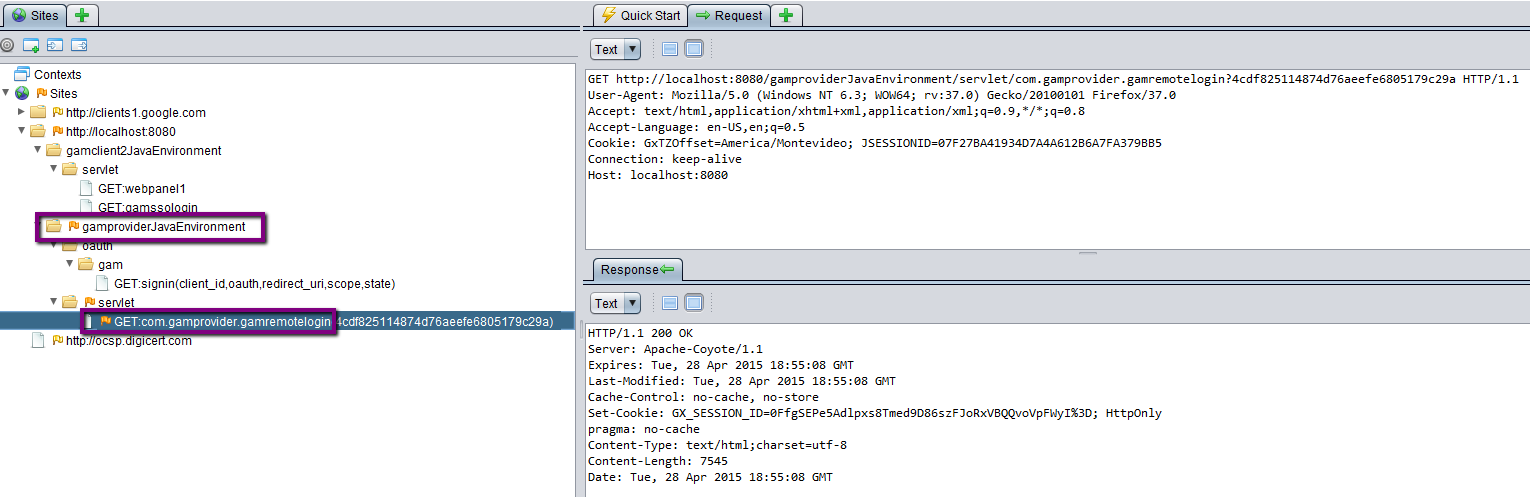
5. After the user enters his credentials, a redirect is done to the redirect URI of step 2. The parameters of this response are used for security checks.
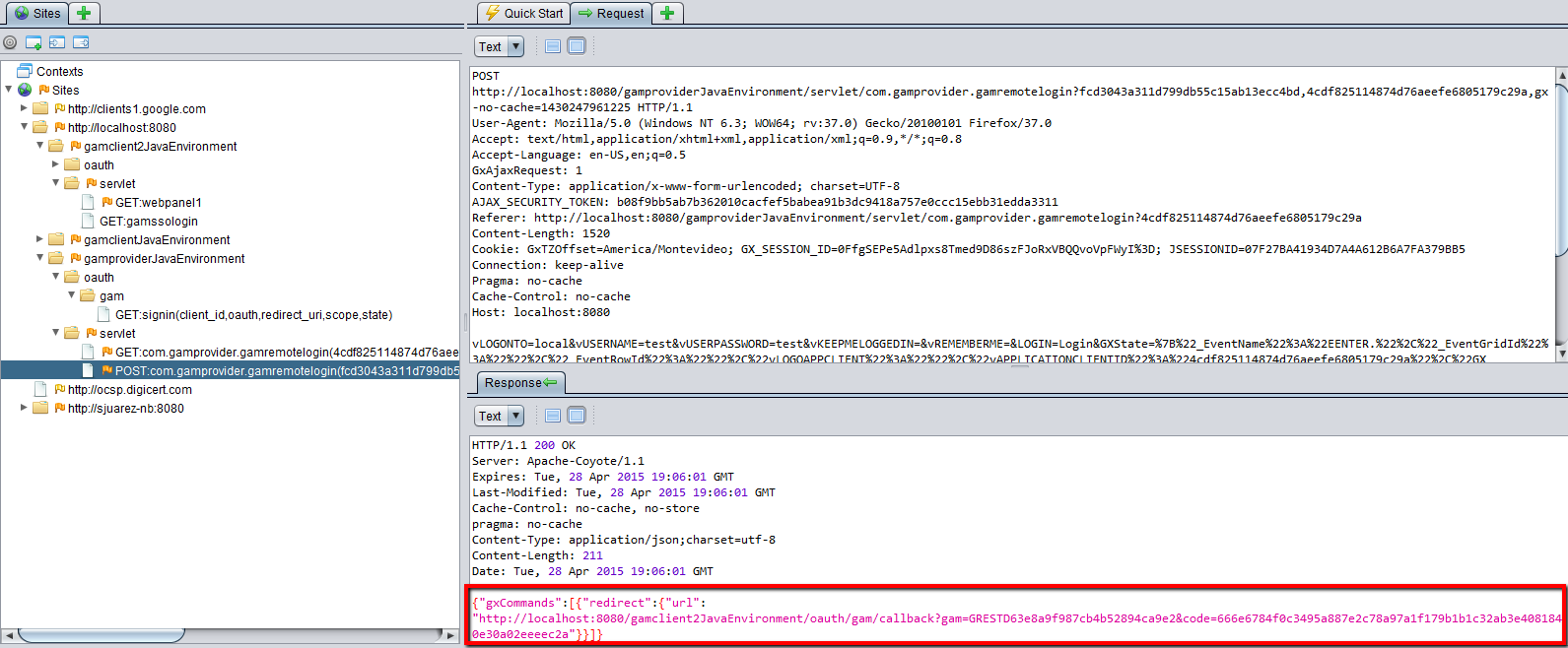
In the meantime, the following POSTS are executed to get the user's information.
POST ..oauth/gam/access_token
To get the Access Token of the application. In the body of the POST HTTP the following variables are sent: code, client_id, client_secret, redirect_uri, grant_type ("authorization_code")
POST oauth/gam/userinfo
This POST returns the user's information, including the extended user attributes, and the user roles. The information sent depends on the scope sent to the server in step2, and the configuration of the application on the server.
6. If there are no errors, the flow returns to the GAMSSOLogin object that runs on the client.
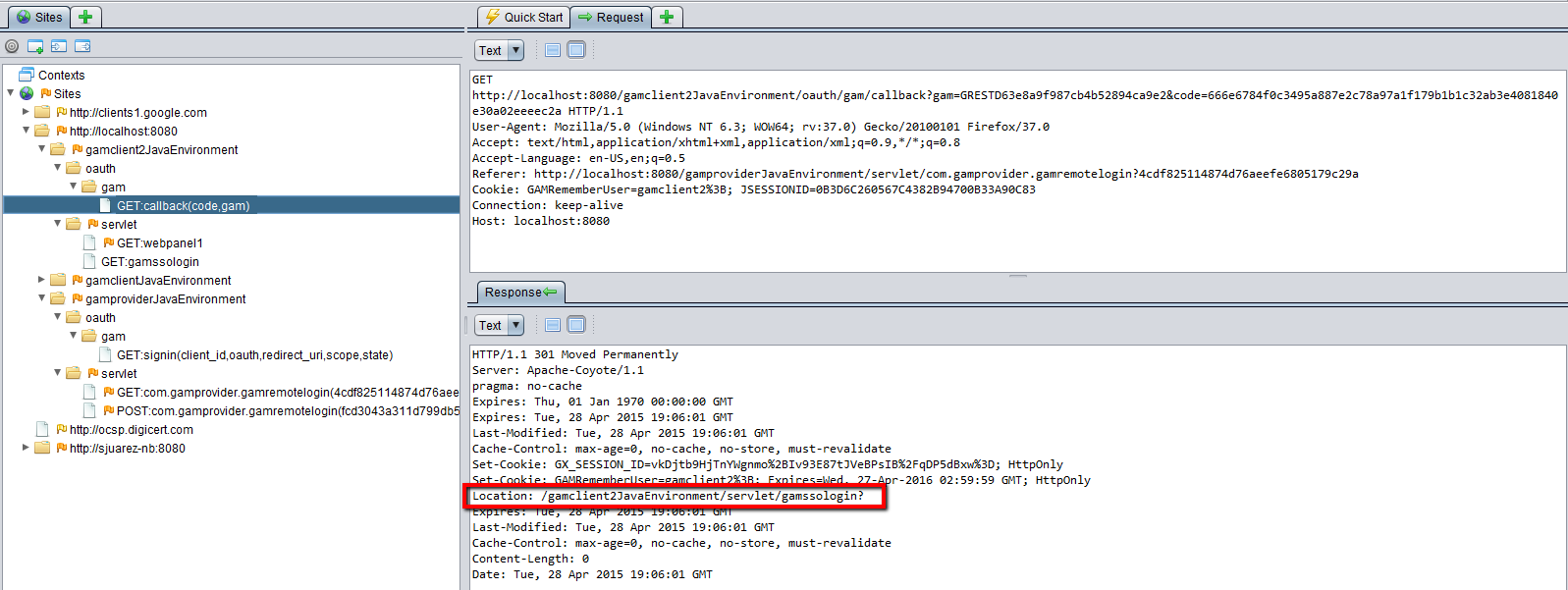
When the session is valid, the GAMSSOLogin object redirects to the web object that had caused the security exception.
Notes:
- We used Owasp ZAP to intercept the traffic and see the request and responses of each call.
- If an encryption key is used for communication between client and server, the information is not in plain text.
GAM SSO flow of execution