Errors may occur once Windows XP Service Pack 2 has been installed, when attempting to establish the connection with the license service (also happens with Windows 2003 and windows 2008 Servers).
The problem arose since this Service Pack introduced several modifications regarding security that affect the DCOM connection between the licenses server and the clients. The possible errors are shown in the following figures and occur when attempting to enter to any tool (GeneXus, GXplorer, GXquery etc.) that uses centralized licenses:
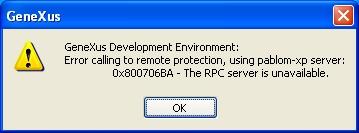
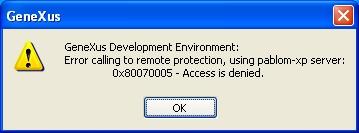
The common solutions for these problems are detailed in Access Denied when using remote licenses - Solution.
First, try the solution listed on that document, and, if the errors still appear, continue with the checklist detailed here. Trying the possible solutions, in the same order as they are listed, is recommended.
1. Disable Windows Firewall
Windows Firewall is installed and turned on by default. If the company has already a Firewall in the network, having Windows Firewall turned on may not be necessary. Therefore, the first option is disabling it. This is performed from Control Panel > Windows Firewall as shown in the figure:
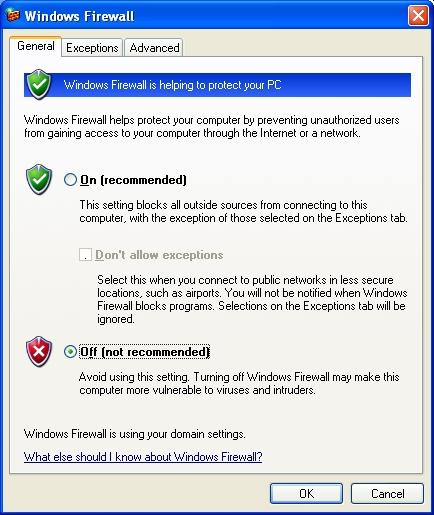
To verify that the Firewall was turned off, it is recommended downloading the service Windows Firewall/Internet Connection Sharing (ICS) in Control Panel > Administrative Tools > Services
2. Enabling DCOM port (135) and applications
Quite often, having the Firewall turned off is not desirable. Therefore, the best option is to include DCOM (135) communications port and the applications (Protection Server, GeneXus, etc.) in the Firewall exceptions. You can set these exceptions in Control Panel > Windows Firewall, Exceptions tab:
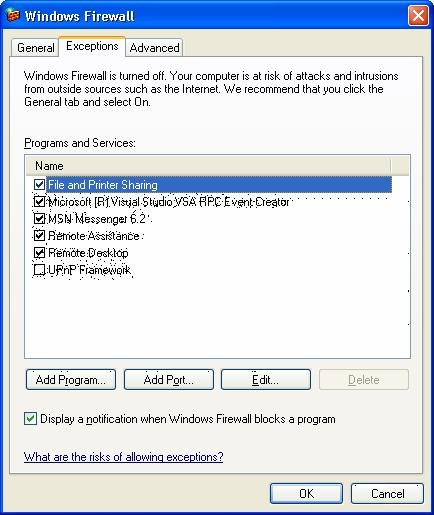
With the "Add Port..." button, you can add 135 port to the exceptions (in the server and in the clients), as shown in the figure:
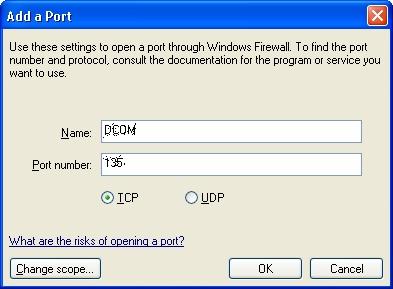
And with the "Add Program..." button, you can add the exceptions to the currently used applications. Specifically, the Protection Server must be added in the server exceptions (ProtSrv.exe). In GeneXus clients, and in other currently installed tools (GXplorer, GXquery, etc.). If the programs are also installed in the license server, they must be also added to the Firewall exceptions.
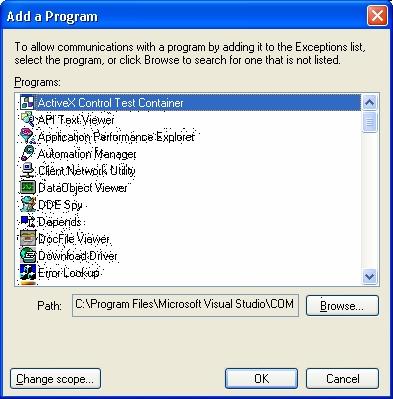
3. Enabling ports range
For the Remote Procedure Calls (RPC)/Distributed Component Object Model (DCOM) protocols, RPC uses Transmission Control Protocol (TCP) port 135, and DCOM uses a nightmarish combination of TCP, User Data Protocol (UDP), ports, and connections.
DCOM is particularly troublesome for firewall access because it dynamically assigns ports to processes. By default, it freely assigns TCP and UDP ports ranging from 1024 to 65535, making it difficult to function securely across a firewall. In addition, new connections are established when responding to a client, meaning that the port the client used for the request is not the same as the port used for the response. Also, DCOM does not support Network Address Translation (NAT), which is among the more common methods of configuring a firewall.
For those cases where you have a local firewall, you may need to enable a fixed port range so that Windows establishes the communications with the license server. You can set this range in two different ways:
- Throughout Component Services (dcomcnfg.exe)
- Altering the Windows Registry (regedit32.exe)
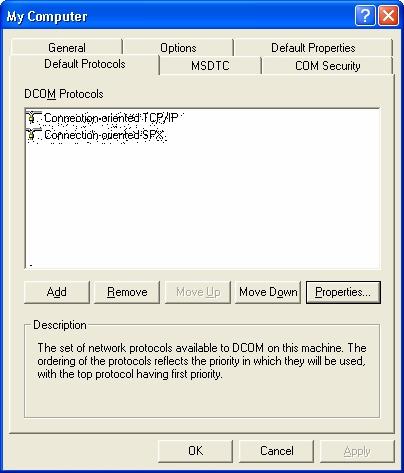
Restrict the range of TCP ports using Component Services:
In Control Panel > Administrative Tools > Component Services, in the left tree go to Component Services > Computers > My Computer and press the Configure My Computer button (selected in the figure below), or right-click on My Computer, in the tree and select Properties.
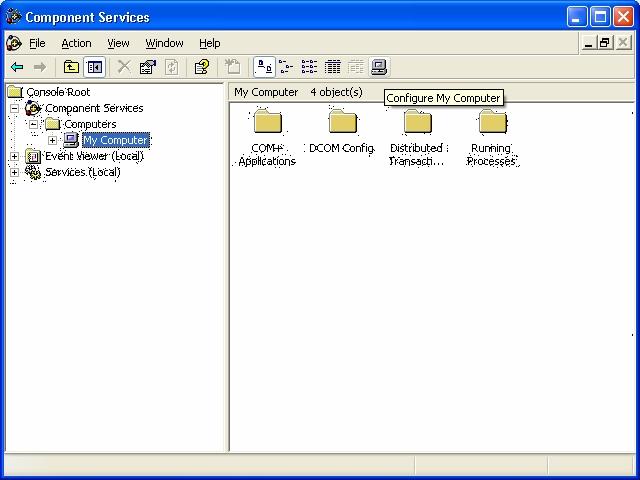
Then, you must select the Default Protocols tab
You must select the TCP/IP protocol and press the "Properties..." button. A window like the following one will be displayed:
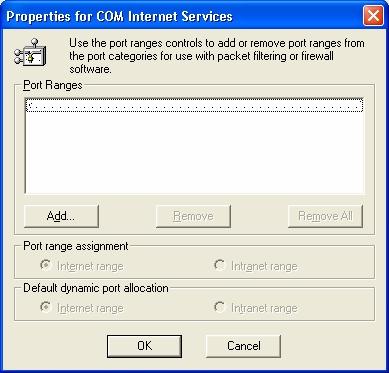
With the "Add..." button, you can enter a fixed ports range to be used; e.g.: 5001-5010
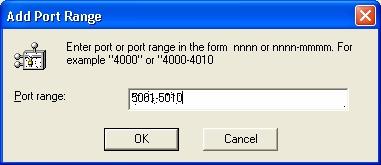
Restrict the range of TCP using Windows Registry:
Create three registry keys under HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\Rcp\Internet using REGEDT32.EXE.
Name = Ports , Type = REG_MULTI_SZ, Value = i.e. (5001- 5010) Specify one port range per line
Name = PortsInternetAvailable, Type = REG-SZ, Value = Y,
Name = UseInternetPorts, Type = REG_SZ, Type = Y or N depending on if you are including or excluding this range.
Reboot the server for registry settings to take effect.
Note that you must use REGEDT32.EXE to configure these settings. REGEDT.EXE currently does not support the REG_MULTI_SZ type required by the ports named value entry. Also, you must reboot your machine any time you make changes to any of the following registry settings in order for them to take effect.
Check the following for more details: http://support.microsoft.com/kb/154596 / http://www.verdiem.com/kb/configure-firewall-dcom-ports
In short, make sure to enable the 135 port and the associated port range detailed above (in the sample 5001-5010) to connect to another machine to get licenses, otherwise, you will get "Access is denied" or "The RPC service is not available" error.
4- Editing DCOM rights (Application)
If the previous steps have not solved the problem, a fourth option would be attempting the edition of the DCOM rights. Firstly, you attempt to edit the DCOM rights for the Protection Server application in the license server. If the license server does not have XP SP2 and the problem continues, you can try with point 5. Go to Control Panel > Administrative Tools > Component Services and then, in the left tree, go to Component Services > Computers > My Computer > DCOM Config and select ProtSrvService in the applications list. Right-click and select Properties.
A screen like the following one will be displayed:
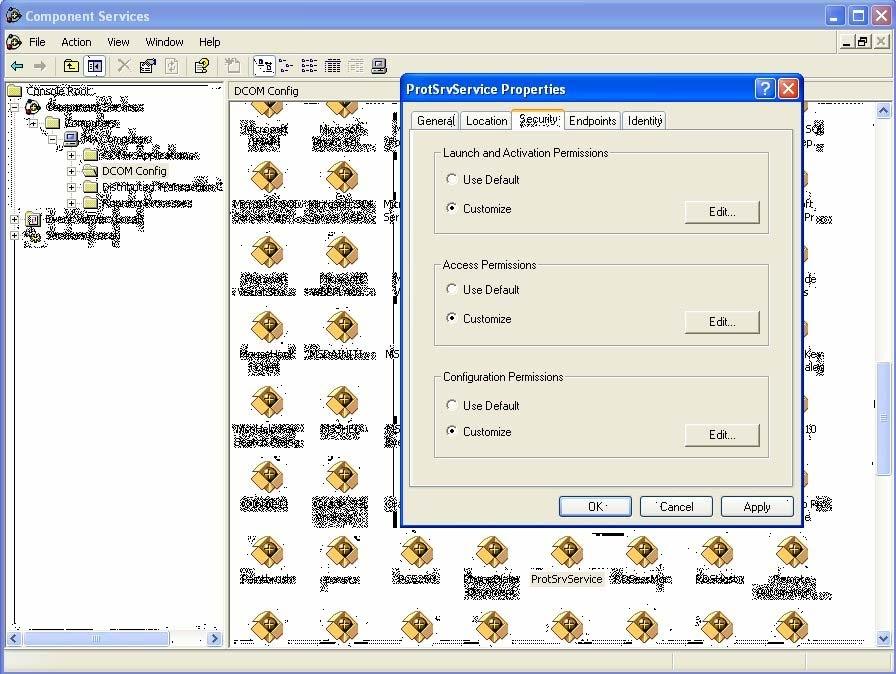
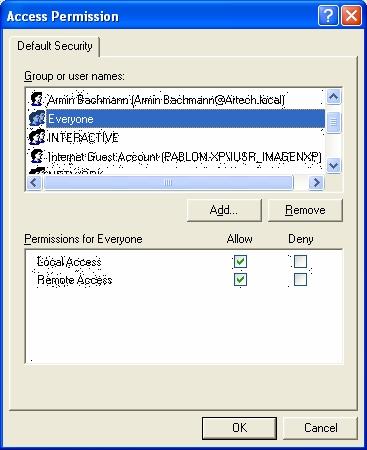
On the screen shown, you must edit the launch and activation rights and the access rights (Launch and Activation Permissions and Access Permissions) by selecting the Customize option and pressing the "Edit..." button. You must select total access (select the four options) for the following groups: Everyone, Network, System, and Interactive, as shown in the following figures:
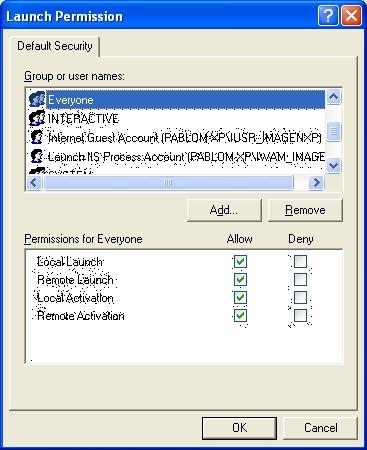
5. Editing DCOM rights (System)
If you have not been able to solve the problem with the previous steps or if after step 3 the problem continues and the license server is not Windows XP SP2, you must try editing the system DCOM rights. This may be performed in the same window where you edit the fixed exit ports range for TCP/IP mentioned in point 3.
Firstly, you must verify that the distributed DCOM is enabled (in Default Properties tab, by selecting Enable distributed COM on this computer. Besides, Default Authentication Level must be in Connect and Default Impersonation Level in Identity.
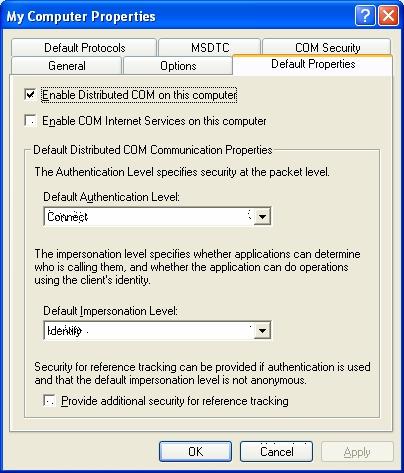
Then, you must set up access and launch rights (Access Permissions and Launch and Activate Permissions) in COM Security tab.
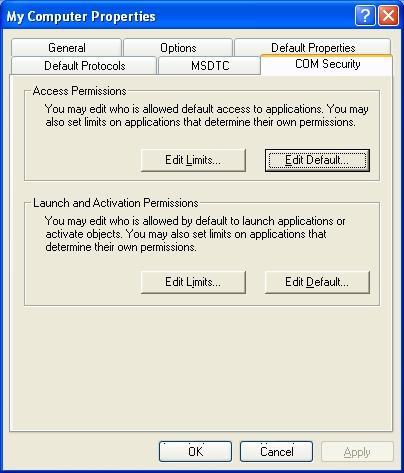
You have to do the same in both places: first, go to "Edit Limits..." button and set the rights (for the group Everyone and ANONYMOUS LOGON), as shown in the following figures:
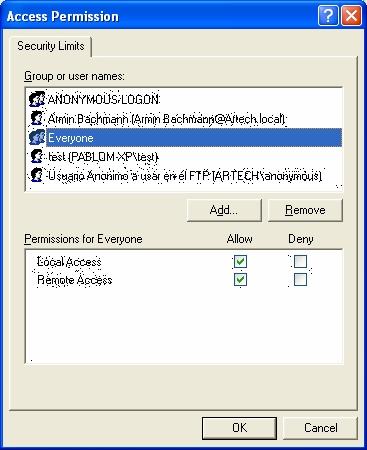
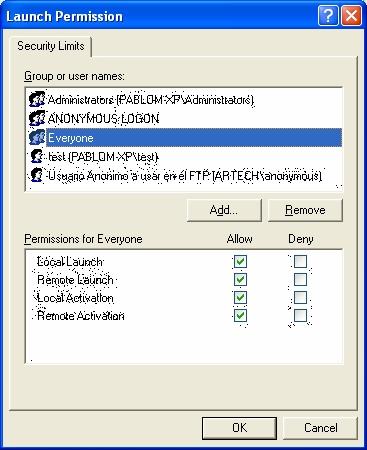
And then, in "Edit Defaults...", you must set up the rights for the following groups: Everyone, Network, System and Interactive, as shown in the following figures.
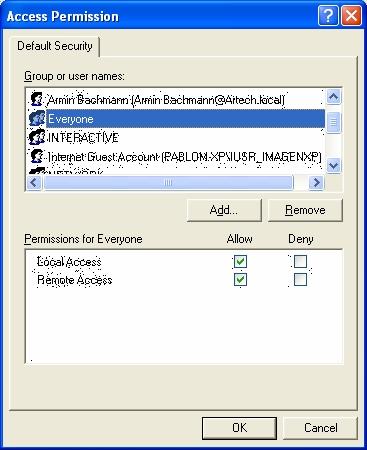
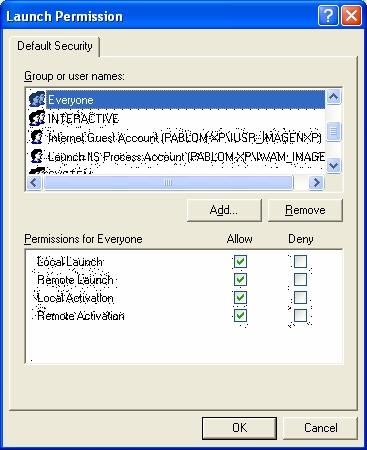
GeneXus 9.0 and older versions
GeneXus 9.0, and older versions, need to make callbacks to the
GeneXus Protection Server. Therefore, a connection is firstly created using port 135 and then a second connection is established from the license server to the client. In order to enable this second connection —from the server to the client—through the firewall, in addition to enabling the connection through port 135, all TCP connections initialized from the server must be allowed.
A port range can be given for these connections, to do so follow the next steps:
- In the server and client PCs, define the DCOM port range as explained in the section "Enabling DCOM port (135) and applications through Windows Firewall".
- In the server PC, allow all outbound connections to the port range used in step 1 and for port 135.
| Note |
| Port 135 and the port range used by DCOM must be enabled in the VPN settings if the client and server are connected through a VPN. |
Notes and References:
Once you have made the different changes in the settings, it is recommended to restart the corresponding PC. It is also recommended to download the service and turn it on again regarding the license server. See SAC 16577 and SAC 9809.
Tool to test the DCOM connection
Security changes in Windows XP Service Pack 2
DCOM Settings for remote access
Use DCOM with firewalls