Below is the recommended Amazon S3 configuration that you should consider when developing with GeneXus. Information is provided on the new defaults for buckets and how to properly configure access properties in Amazon S3 to ensure smooth integration with GeneXus.
Changes to the default security settings of S3 Buckets can affect the behavior of your GeneXus-developed applications. To ensure smooth integration between GeneXus and Amazon S3, it is important to configure your S3 bucket with the following settings:
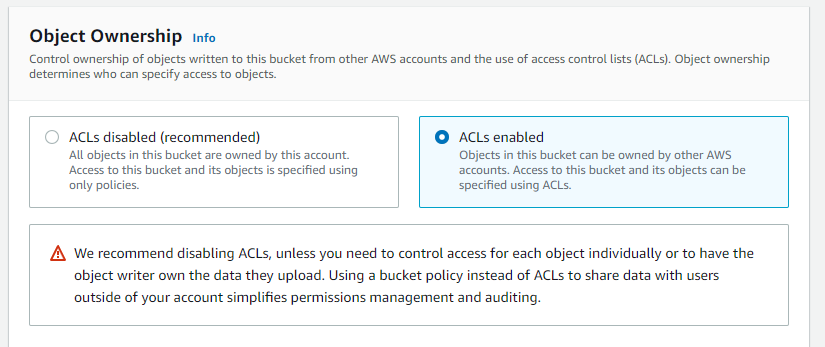
While Amazon has disabled Access Control Lists (ACLs) by default for new buckets, GeneXus requires ACLs to be enabled for proper functionality. Configure your bucket to have ACLs enabled.
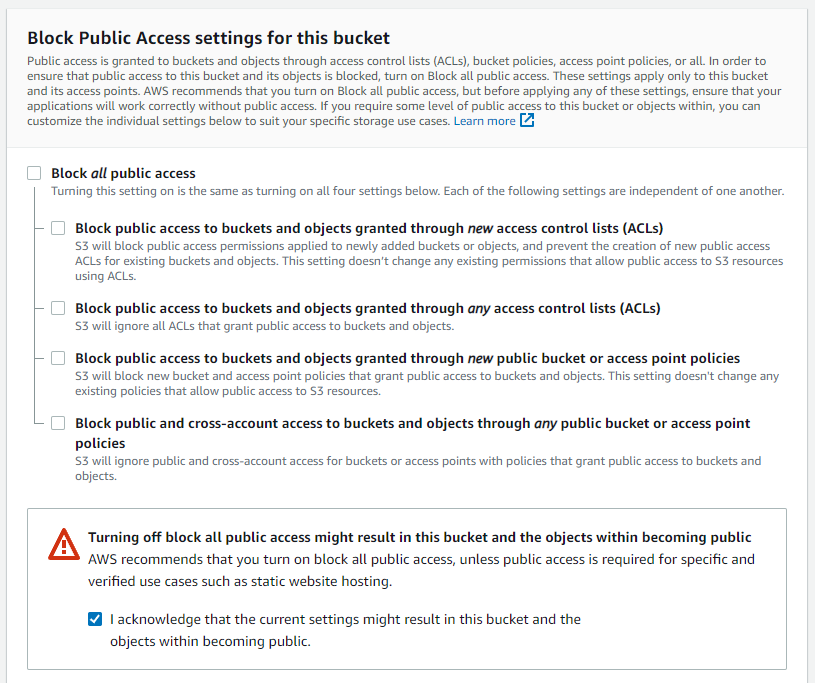
To work with Privacy = PublicRead, disable the "Block all public access" setting for allowing public read access to the objects in the bucket. However, if the entire bucket's contents should be private, you can leave the "Block all public access" setting enabled.
It's important to note that these settings ensure compatibility between GeneXus and Amazon S3, allowing you to manage access permissions effectively and securely. However, it's recommended to review the detailed information for a better understanding of the changes and their impact on GeneXus applications. A brief summary of the changes is provided below.
As of April 2023, Amazon S3 automatically implemented S3 Block Public Access configuration and disabled ACLs for new S3 buckets. That is, buckets created by default in Amazon S3 have the following configurations:
Block Public Access: Enabled (Block Public Access = TRUE)
ACL (Access Control Lists): Disabled (ACL = OFF)
The first configuration, S3 Block Public Access, is designed to prevent unwanted public access to S3 buckets and their objects. Enabling S3 Block Public Access ensures that new buckets have settings that block public access by default. This helps prevent security incidents and protects the data stored in S3 buckets.
The second configuration involves disabling S3 access control lists (ACLs). ACLs are an access control mechanism previously used in S3 to define specific permissions on buckets and objects. However, Amazon has decided to disable this functionality by default in the new buckets.
Instead, Amazon S3 now recommends using Identity and Access Management (IAM) policies to manage access permissions to S3 buckets and objects. IAM policies provide greater flexibility and control over permissions and are the recommended way to manage access to S3 resources.
Amazon S3 will automatically enable S3 Block Public Access