Warning: This article refers to advanced configurations when you are working with the Security Scanner extension. If you are working with the Security Scanner built-in tool, read about the advanced configurations
here.
The advanced configurations are available since the GeneXus Security Scanner extension 3.8.3.0 version.
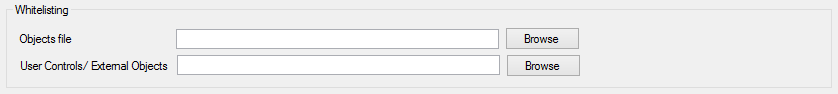
To exclude from the Security Scanner results that objects the analyst already reviewed and estimates are safe a whitelist can be added to the analysis.
The whitelist for this case is an XML file uploadable from the Whitelist section on the object files block with this structure:
<?xml version="1.0" encoding="UTF-8"?>
<suppress>
<codes>
<codesItem>
<codenumber>100</codenumber>
<objects>
<object>obj_name_1</object>
<object>obj_name_1</object>
<object>obj_name_1</object>
</objects>
</codesItem>
<codesItem>
<codenumber>101</codenumber>
<objects>
<object>obj_name_1</object>
<object>obj_name_1</object>
<object>obj_name_1</object>
</objects>
</codesItem>
</codes>
</suppress>
This implementation allows the analyst to configure objects by name to exclude by rule, the objects will not be excluded from all the analysis, just for the rules specified. Be aware the casing is ignored.
An SDTis available to create some whitelist automation.
The XML Schema for validation or integration is also available.
To exclude from the Security Scanner results on rules #120 and #121 that External Objets and User Controls the analyst already reviewed and estimates are safe a whitelist can be added to the analysis.
The whitelist for this case is a CSV file uploadable from the Whitelist section on the User Controls/External Objects block with this structure:
EOname1, EOName2, UCname1, UCName2, EOName3, UCName4
Be aware the casing is ignored and only the "," is taken as a valid separator character. The ";" is not a valid separator character for this file.
The User Controls and External Objects can be mixed, both go on the same file, and order is not taken to account.
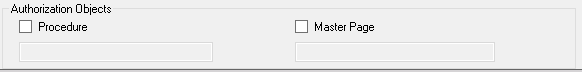
In some cases, developers avoid the use of GAM on The KB or some objects on a KB. In those cases, the common practice is to use an Authentication or Authorization procedure at the beginning of an object execution or inside the Master Page. This feature is made to adapt to those cases. This configuration applies only to rule #102.
Use this feature only if you are certain the procedure is used at the beginning of the execution. It does not distinguish the position of the procedure call inside the object. Be aware the casing is ignored.
To configure an Authorization/Authentication procedure go to the Authorization Objects section and click on the Procedure Checkbox. It will enable the textbox to write de Authentication/Authorization procedure's name.
It will review Procedures HTTP, REST and SOAP, Transactions and Web Panels.
To configure an Authorization/Authentication Master Page go to the Authorization Objects section and click on the Master Page Checkbox. It will enable the textbox to write de Authentication/Authorization Master Page's name.
It will review Transactions and Web Panels.