This article describes the GeneXus Access Manager (GAM) Endpoints in order to explain authentication with GAM as IDP using OAuth 2.0 REST services.
Unlike the article HowTo: Use GAM as an OAuth 2.0 provider where this concept is applied within GAM itself, this article explains how it can be used by any external client.
OAuth 2.0 REST service flow with GAM Endpoints as IDP (Identity Provider):
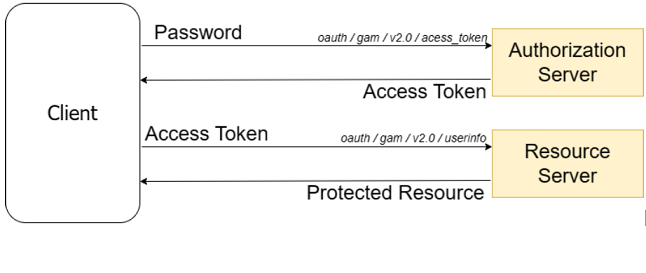
The possible endpoints to authenticate with GAM as IDP are as follows:
1. Access Token
2. User Info
3. Refresh Token
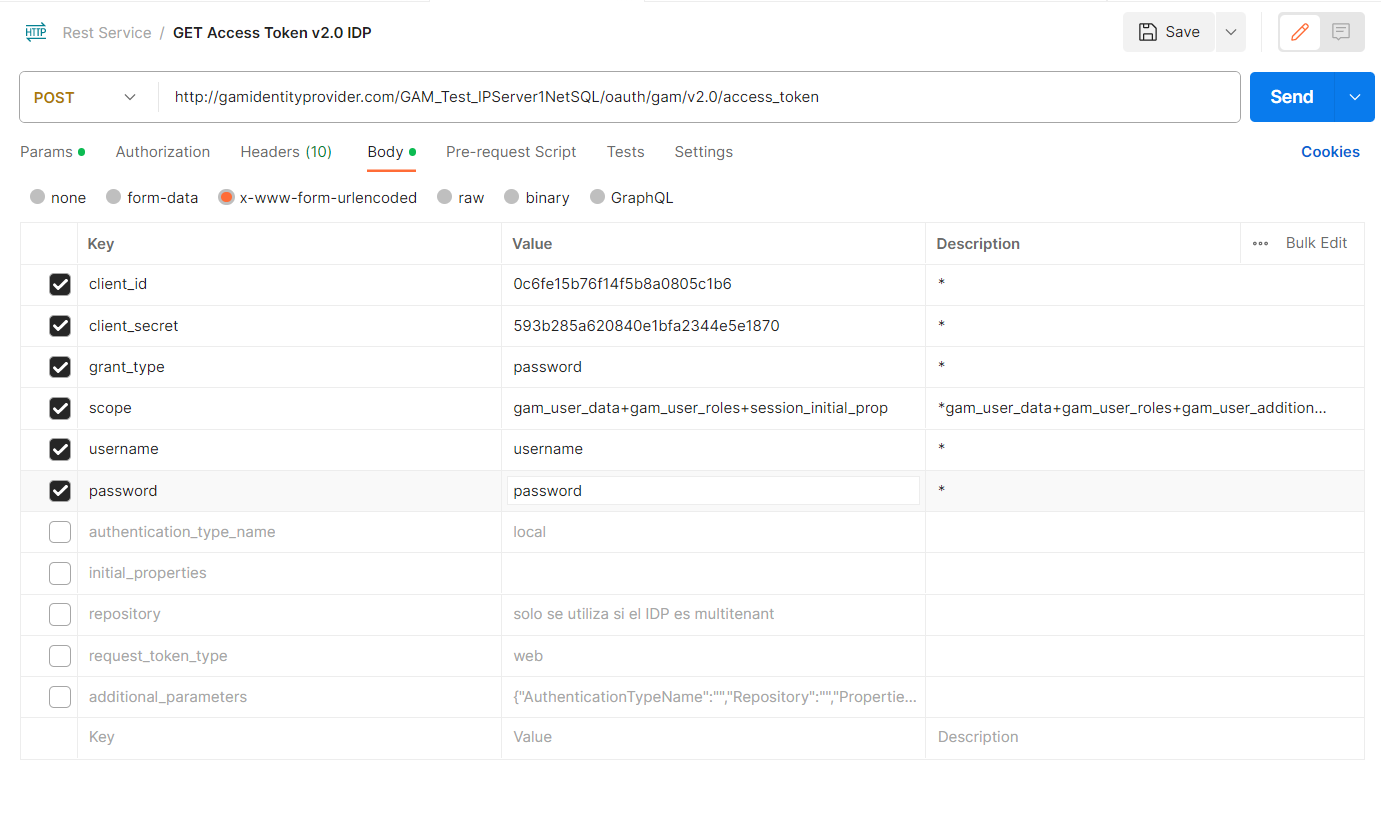
1. Access Token
access_token: Sends the user credentials to get a new Token.
http://<domain-url>/<base-url>/oauth/gam/v2.0/access_token
Content-Type: application/x-www-form-urlencoded. Type of content that will be returned.
Body in Postman
| Tag |
Value |
Description |
| *client_id |
|
Application Client ID. |
| *client_secret |
|
Application Client Secret. |
| *grant_type |
password |
In this case, it must be ‘password’. |
| *scope |
gam_user_data+gam_user_roles |
Scope of the user account you want to access. |
| *username |
|
Username of the user to be authenticated. |
| *password |
|
Password of the user to be authenticated. |
| authentication_type_name |
local |
Authentication type name; by default, it uses the default Authentication Type of the Repository. |
| initial_properties |
|
User custom properties array. |
| repository |
|
Only use if the IDP is multitenant. |
| request_token_type |
OAuth |
Determines the token type to return and, based on that, the Security Policy to be applied. By default it is OAuth, and the other possible value is Web. |
additional_parameters: Use if you want to get more user information.
Check possible Scopes: OAuth User Scopes.
[{"Id":"Company","Value":"GeneXus"},{"Id":"Branch","Value":"Uruguay"}]
{
"access_token": "ae47229f-e133-42d1-87e0-c5ac59e51edf!c0f5aadd56fb7e1305e7c7abac8ee497d8d640ab446af07149fba8b2a3cad8321ad3c052dd65a7@SSORT!ae47229f-e133-42d1-87e0-c5ac59e51edf!0c6fe15b76f14f5b8a0805c1b6c20",
"token_type": "Bearer",
"expires_in": 0,
"refresh_token": "",
"scope": "gam_user_data+gam_user_roles+session_initial_prop",
"user_guid": "736c85fa-5123-437d-a528-93471d3bae42"
}
This response follows the GAMOAuth20AccessToken External Object structure.
Note: To receive a refresh token, you must change the default value of the property Maximum OAuth token renewals in GAM Security Policies, and set the time that this Token will take to expire.
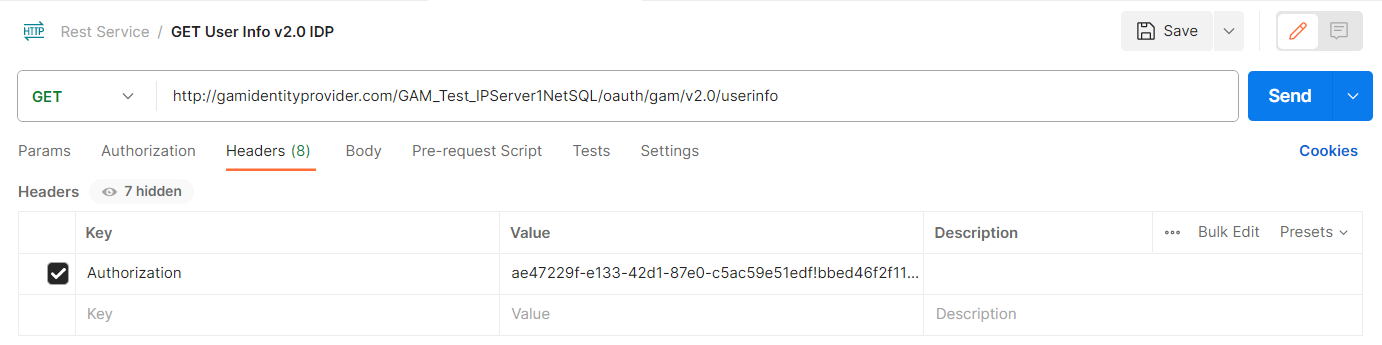
userinfo: Send the access_token obtained in the previous request and get the user info depending on the scopes you have indicated.
http://<domain-url>/<base-url>/oauth/gam/v2.0/userinfo
Content-Type: application/x-www-form-urlencoded. Type of content that will be returned.
Authorization: access_token obtained.
{
"guid": "492c664b-8831-4efb-8618-0c8e86e75446",
"username": "admin",
"email": "admin@example.com",
"verified_email": true,
"first_name": "Administrator",
"last_name": "User",
"external_id": "",
"birthday": "2000-01-01",
"gender": "N",
"url_image": "https://",
"url_profile": "",
"phone": "+598",
"address": ".",
"city": ".",
"state": ".",
"post_code": ".",
"language": "Eng",
"timezone": ".",
"application_data": "",
"CustomInfo": "",
"roles": [
"is_gam_administrator"
]
}
This response follows the GAMOAuth20UserInfo External Object structure.
access_token: In this case, you send a refresh token to get a new Token.
http://<domain-url>/<base-url>/oauth/gam/v2.0/access_token
Headers
Content-Type: application/x-www-form-urlencoded. Type of content that will be returned.
| Tag |
Value |
Description |
| *client_id |
|
Application Client ID. |
| *client_secret |
|
Application Client Secret. |
| *grant_type |
refresh_token |
In this case, it must be “refresh_token”. |
| *refresh_token |
|
|
Postman Example: 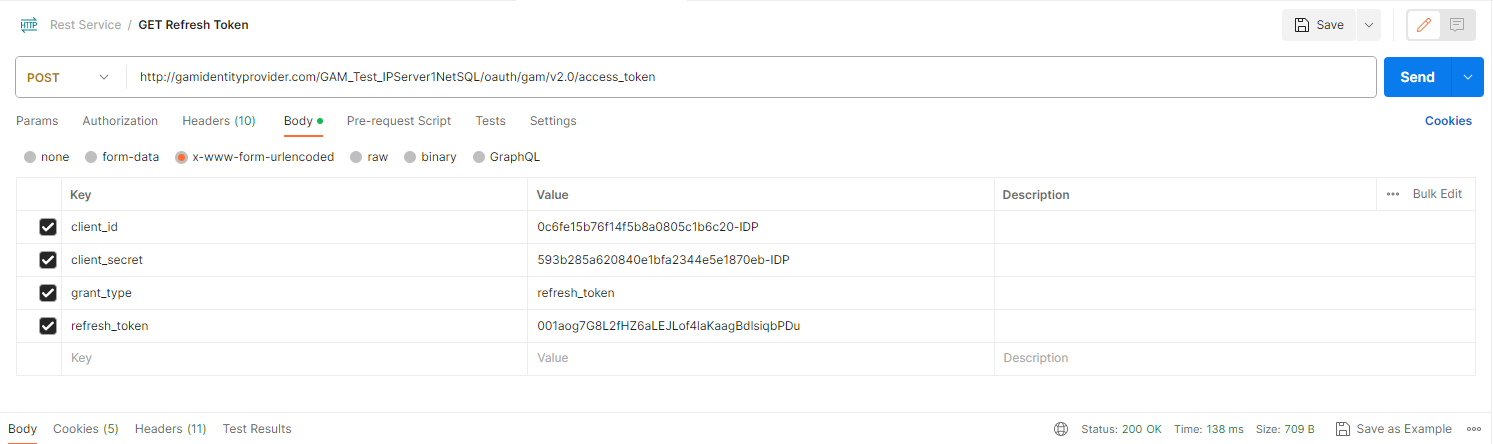
{
"access_token": "ae47229f-e133-42d1-87e0-c5ac59e51edf!f5b06a969d6ca0a6824318bad9fddd3d72913c1e9118ff9d34a4d117c2f6caa749586f4fee99f2@SSORT!ae47229f-e133-42d1-87e0-c5ac59e51edf!0c6fe15b76f14f5b8a0805c1b6c20-IDP",
"token_type": "Bearer",
"expires_in": 6000,
"refresh_token": "002iKhdKkZ5Xa1el62k2elnwQ24sg0fxwM8rYZc",
"scope": "gam_user_data+gam_user_additional_data+gam_session_initial_prop+gam_user_roles",
"user_guid": "492c664b-8831-4efb-8618-0c8e86e75446"
}
HowTo: Use GAM as an OAuth 2.0 provider
GAM - OAuth 2.0 Endpoints to use GAM as Web IDP Server