This document explains the steps to follow in Azure and GAM to configure authentication with Azure as IDP for GeneXus Access Manager (GAM) using SAML 2.0 Authentication type.
1. Go to the Azure website.
2. Once logged in, go to Enterprise applications and select "+ New application".
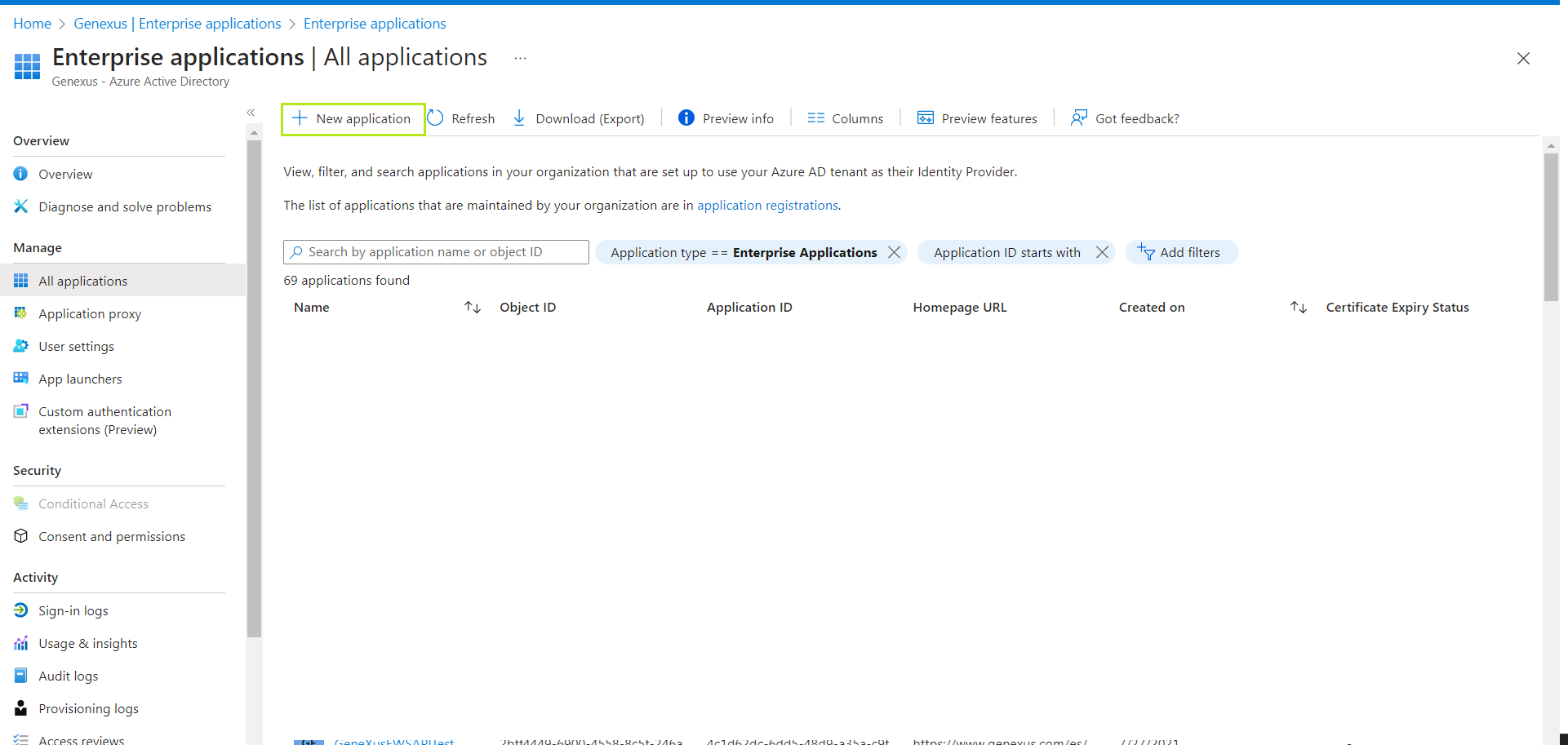
3. Next, click on "Create your own application".
4. After entering a name for your application, a screen like this will appear:
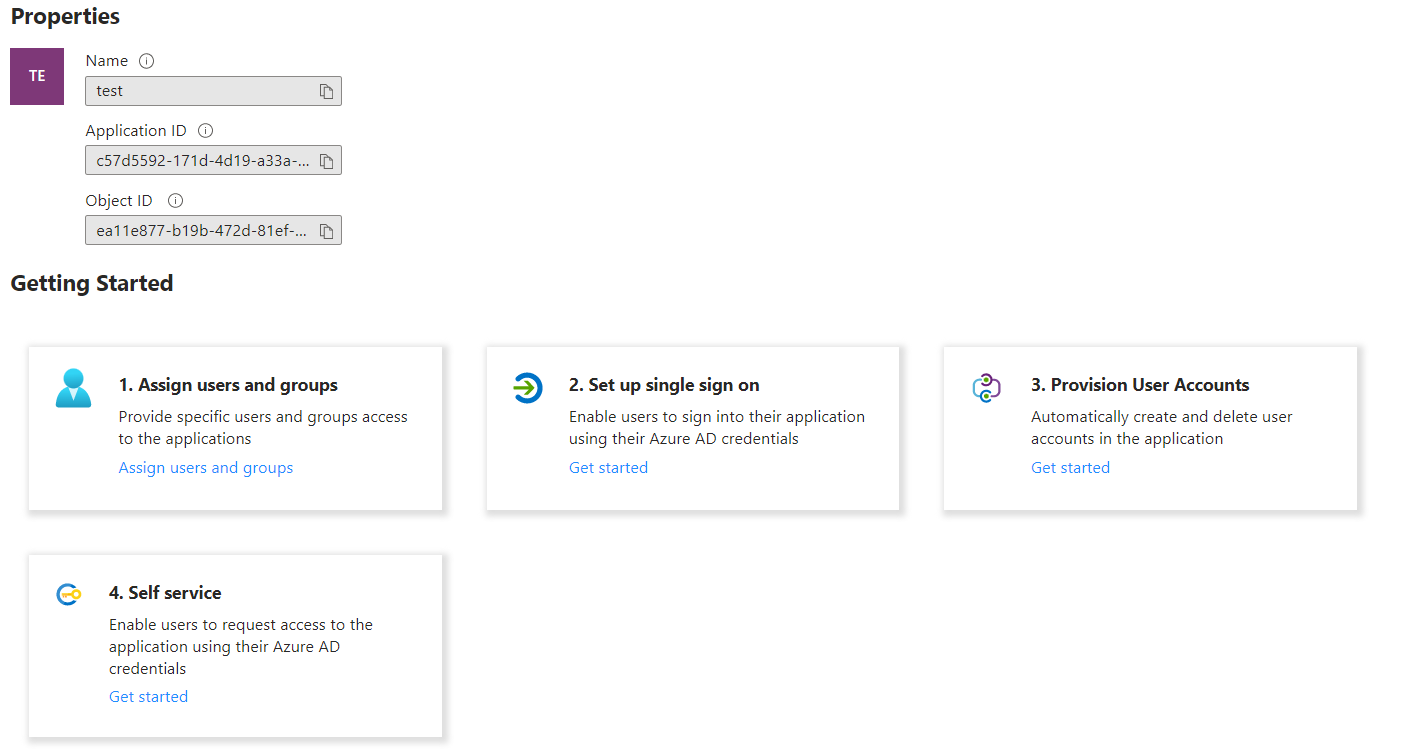
5. Save your Application ID and Object ID. Click on "Set up single sign on" and select SAML.
6. Here you must fill in all the required fields. To do so, select "Edit".
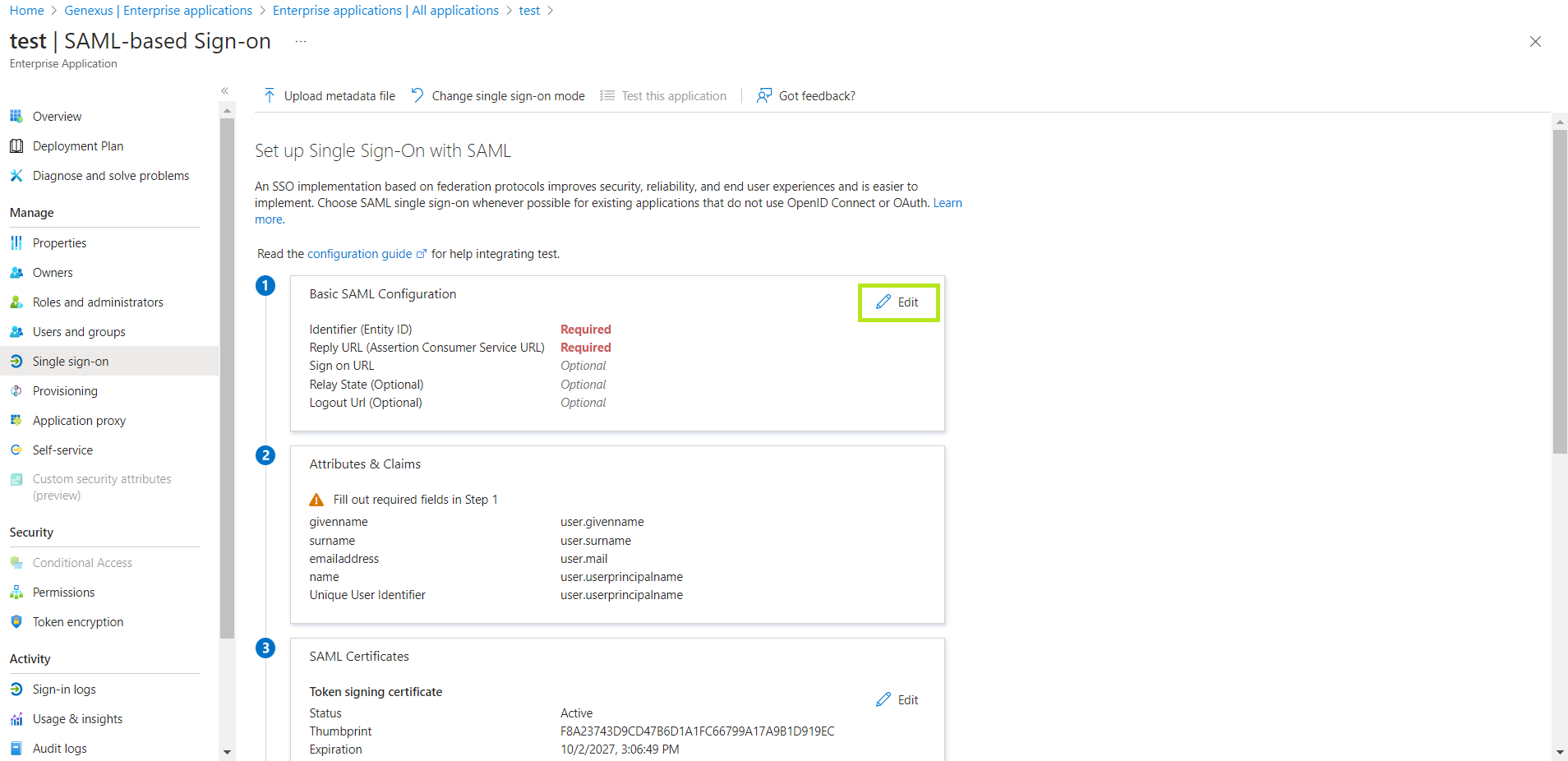
Next, you will see the following screen:
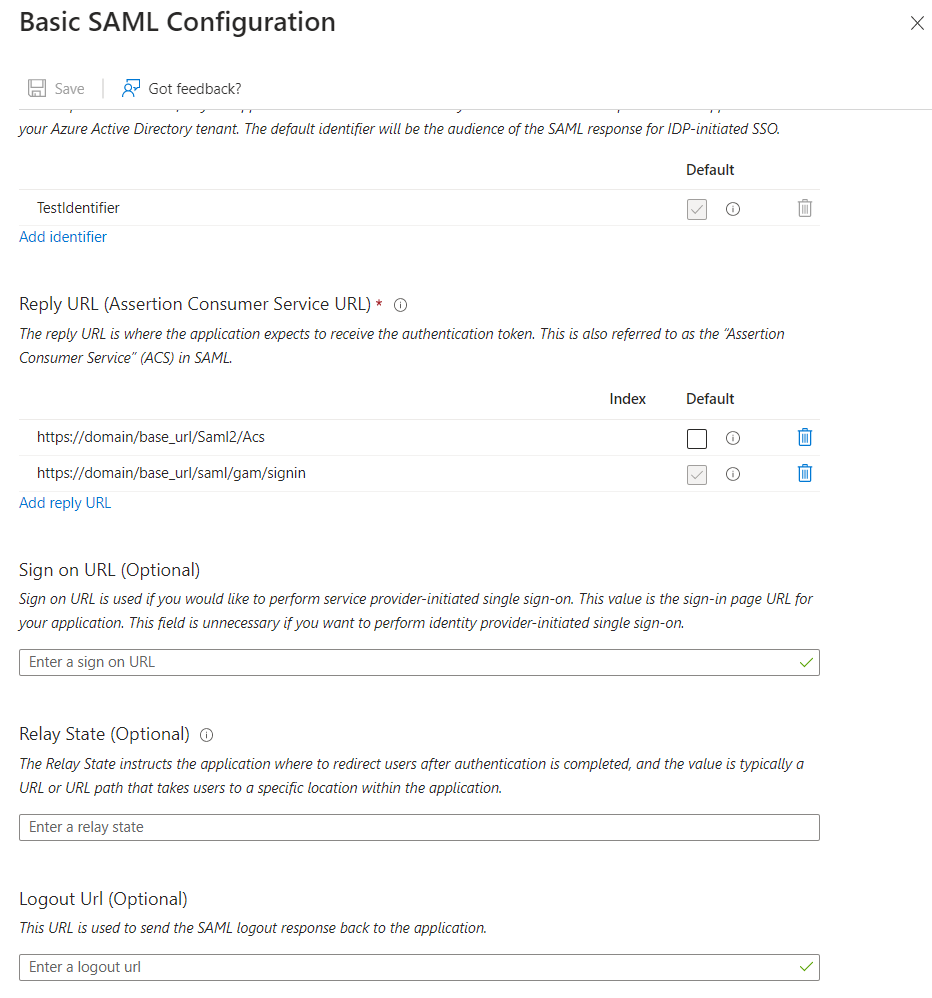
The required information depends on the generator you are using:
- Java: https://<domain>/<base_url>/saml/gam/signin
- Net: https://<domain>/<base_url>/Saml2/Acs
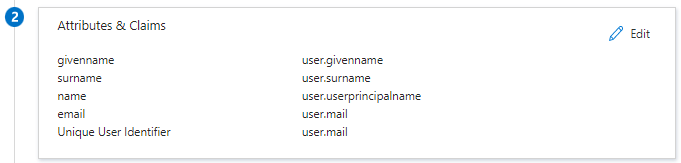
7. "Attributes & Claims" should look as follows:
8. In the "SAML Certificates" section, download Certificate (Base 64).
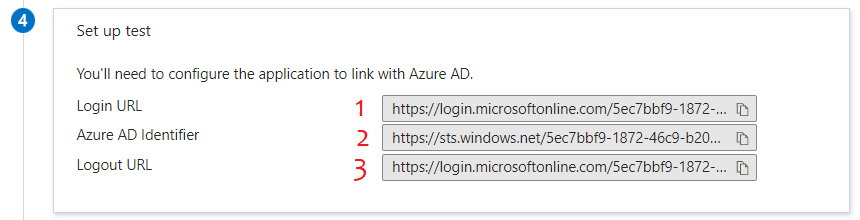
9. The "Set up test" section shows endpoints that will be useful in the GAM Backoffice configuration.
10. Finally, select "Users and Groups" in the left panel (under "Manage") and add some users or your own user.
Distinctive aspects of this configuration:
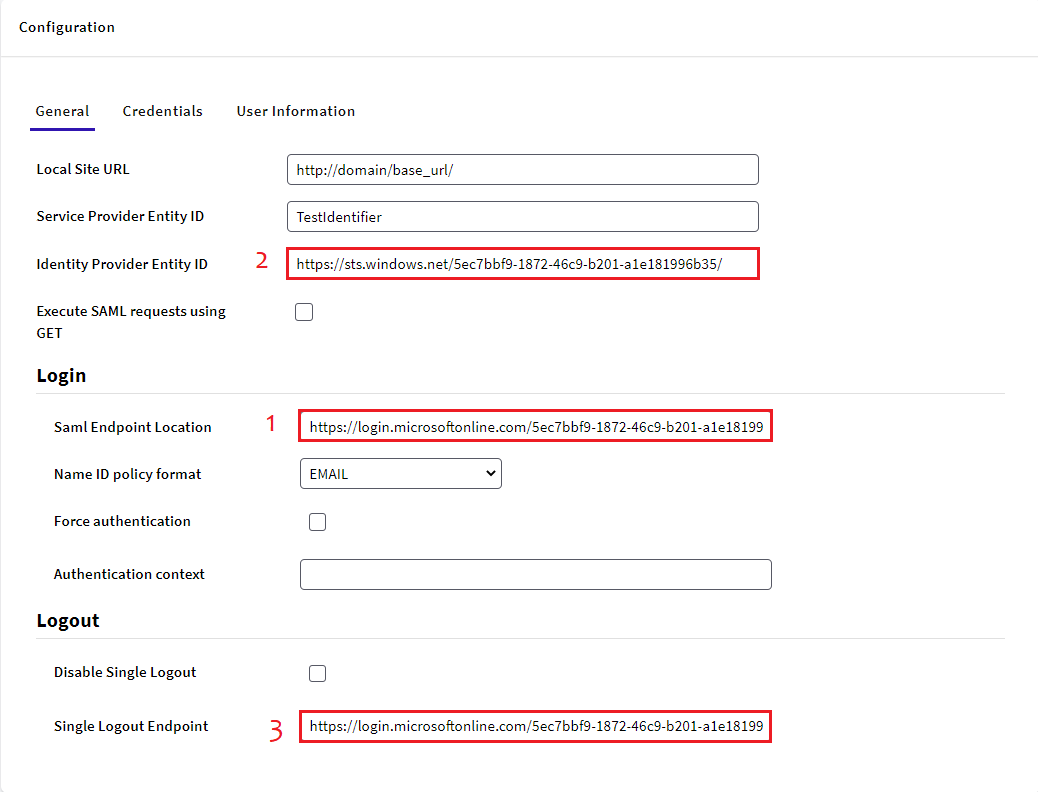
In the case of Java, you must fill the property "Authentication context" with the value "urn:oasis:names:tc:SAML:2.0:ac:classes:Password".
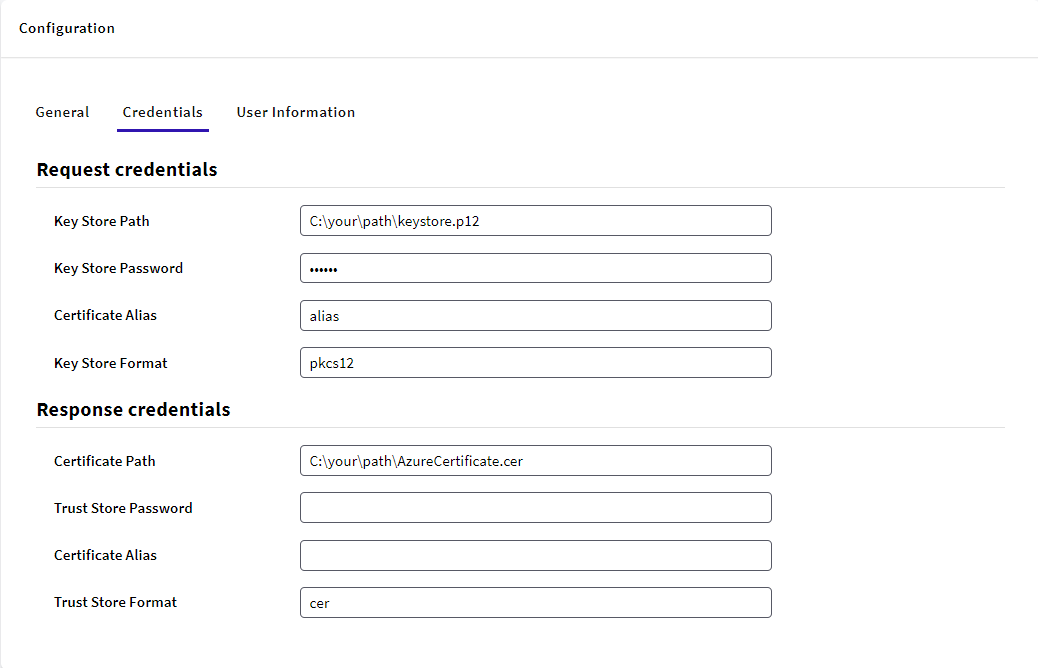
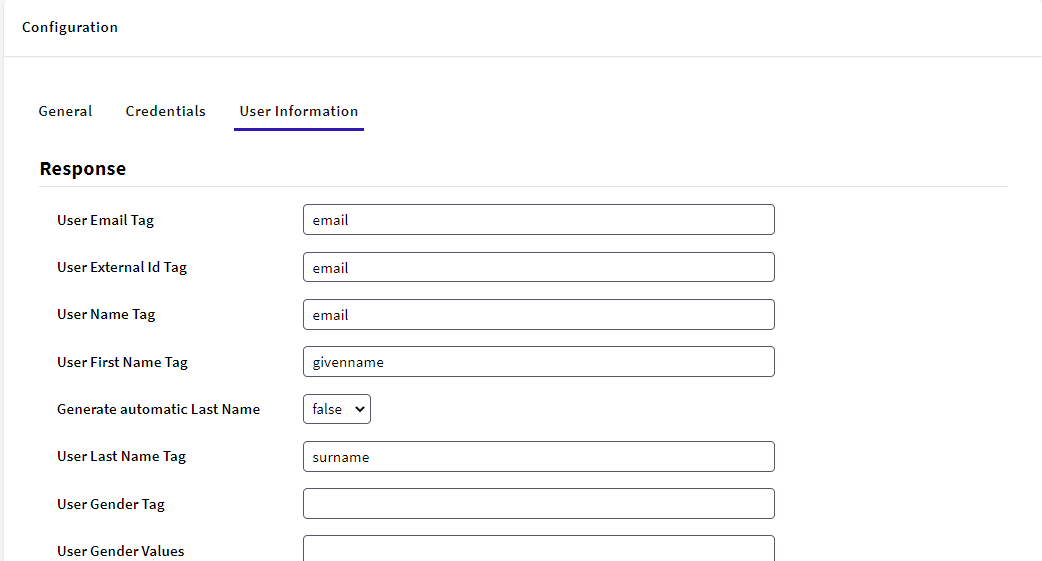
Here you use your Attributes & Claims recently configured.
Note: This is a default configuration; the information retrieved always depends on the IDP configuration (Azure).
If you are getting an error like this:
Received message contains unexpected InResponseTo "id9ab431ed1e434dba80c0562d2e2b48a8". No cookie preserving state from the request was found so the message was not expected to have an InResponseTo attribute. This error typically occurs if the cookie set when doing SP-initiated sign on have been lost.
Please read here how to solve it.
Configure the Environment properties
SameSite cookie attribute = Do not Specify
Parameter Style = Positional.
SameSite cookie attribute = None
Parameter Style = Positional
GAM - SAML 2.0 Authentication type
HowTo: Generate certificates for authentication using SAML 2.0 GAM Authentication