This document explains the steps to be followed in SAP Cloud Platform in order to configure GeneXus Access Manager (GAM) to authenticate using SAML 2.0 Authentication type using SAP.
- Contract the service SAP Cloud Platform Identity Authentication
- Create the certificates necessary to connect to SAP as an SAML 2.0 Identity Provider.
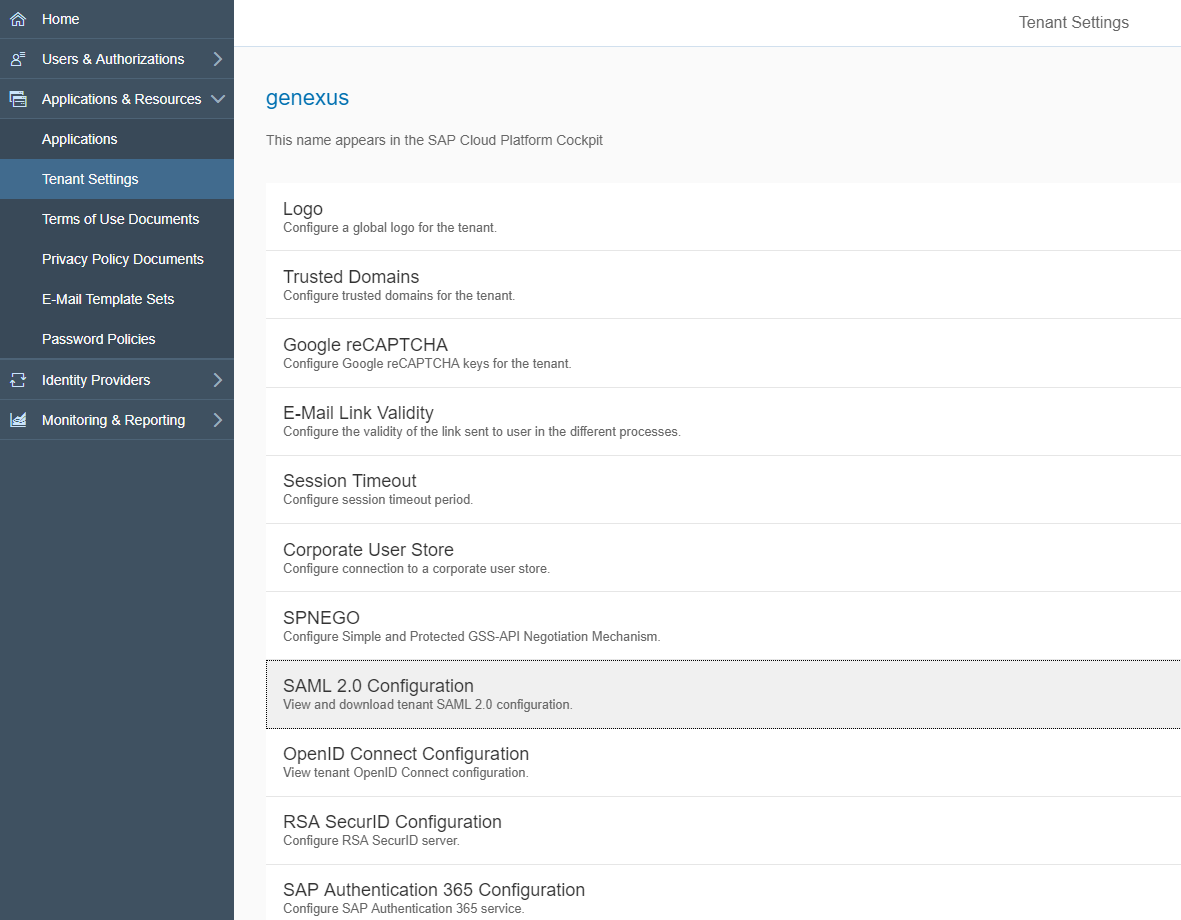
Get the Response certificates from the SAP Cloud Platform Identity Authentication console. Go through Applications > Resources >Tenant Settings > SAML 2.0 Configuration, and click "download metadata".
Generate a Response certificate for SAP (keystore). It's used to complete the Response Credentials section, in the SAML 2.0 Authentication type configuration. For detailed information on the subject, see HowTo: Generate certificates for authentication using SAML 2.0 GAM Authentication.
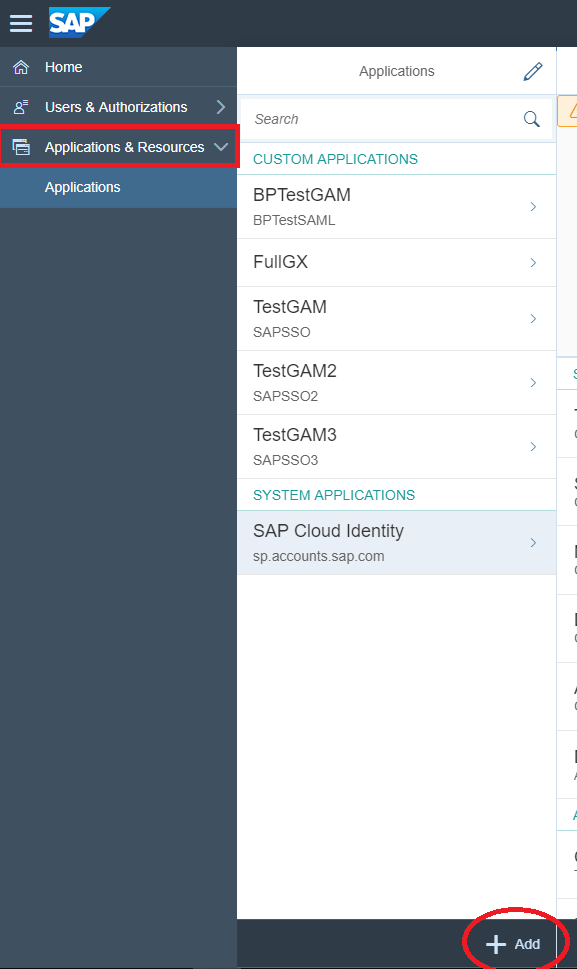
- Create an application in SAP Cloud Platform Identity Authentication. Go through Applications & Resources > Applications, and click "Add".
- Assign a name to the application just created and save.
- To configure the application, go through the Trust option, and configure the Authentication type (by default, it will be SAML 2.0).
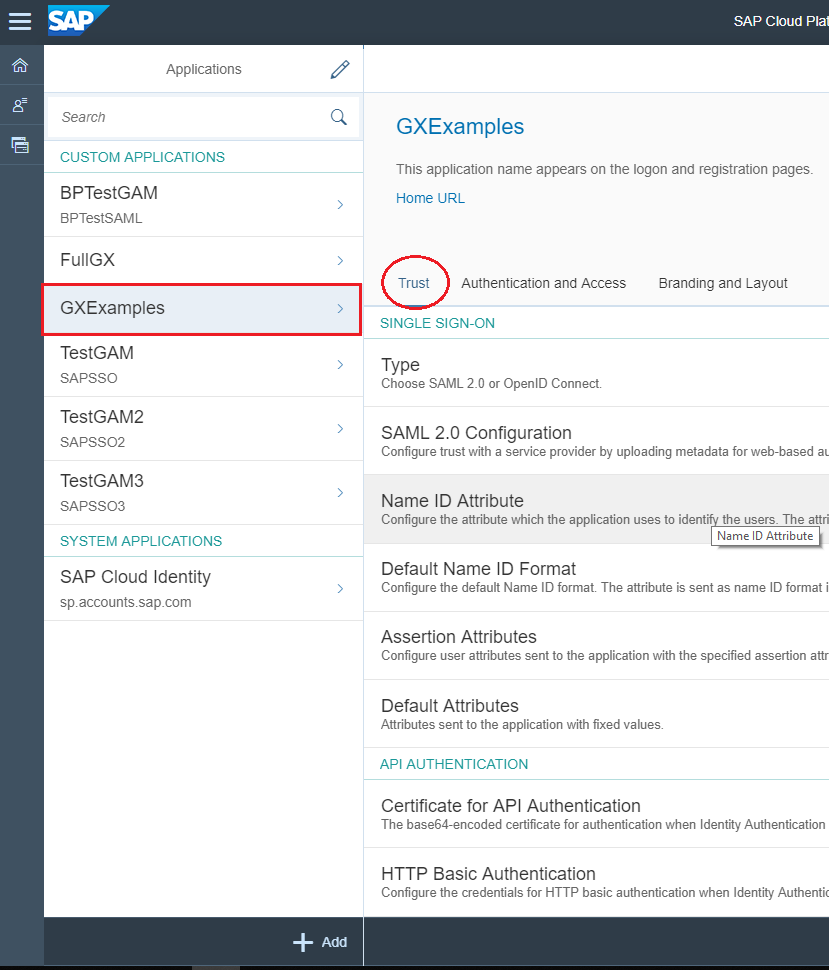
- Select SAML 2.0 Configuration:
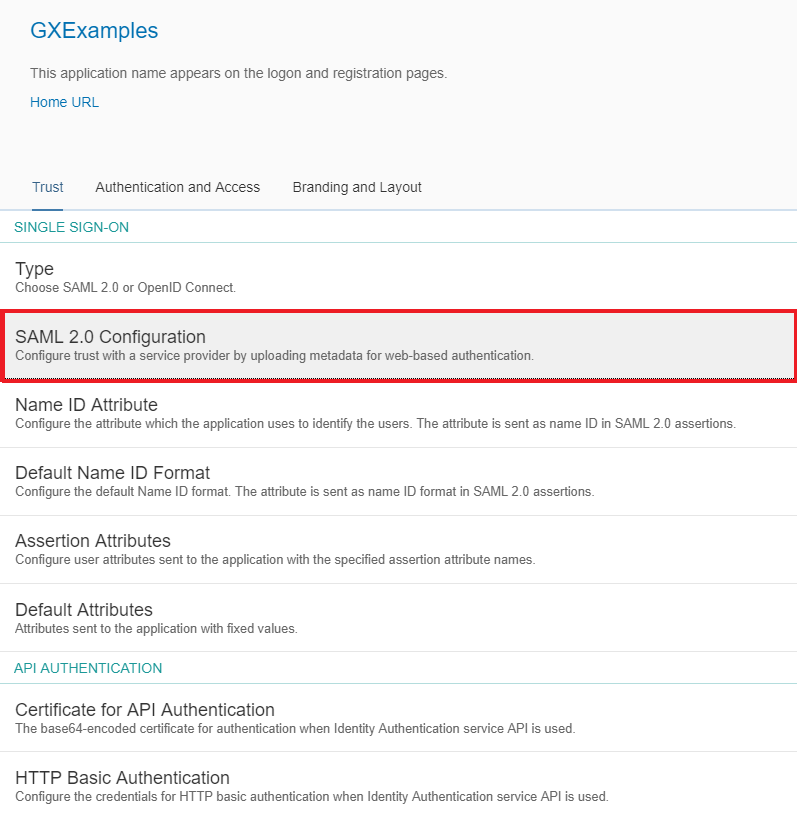
Then configure:
- Name: the external identifier that will be assigned to the application (the same to be configured at the Service Provider Entity ID in the SAML 2.0 Authentication type Login General tab configuration).
- Assertion Consumer Service Endpoint: the URL of the Service Provider (the GeneXus application) that receives responses from the Identity Provider (e.g.: https://gxexample/KBExample/saml/gam/signin).
Important: The format of the URL must be https://<domain>/<url_base>/saml/gam/signin
- Single Logout Endpoint: the URL of the single logout endpoint of the Service Provider (e.g.: https://gxexample/KBExample/saml/gam/signout)
Important: The format of the URL must be https://<domain>/<url_base>/saml/gam/signout
- Signing Certificate: public key used by the Service Provider to sign the requests to the Identity Provider (the certificate.pem created previously).
- Algorithm: the algorithm for signing the response messages.
In the GAM backend, you'll have a screen like the one below:
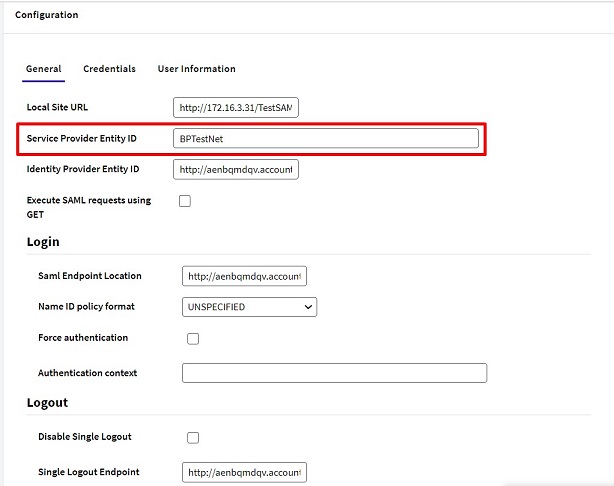
Authentication Context: Leave it empty for SAP.
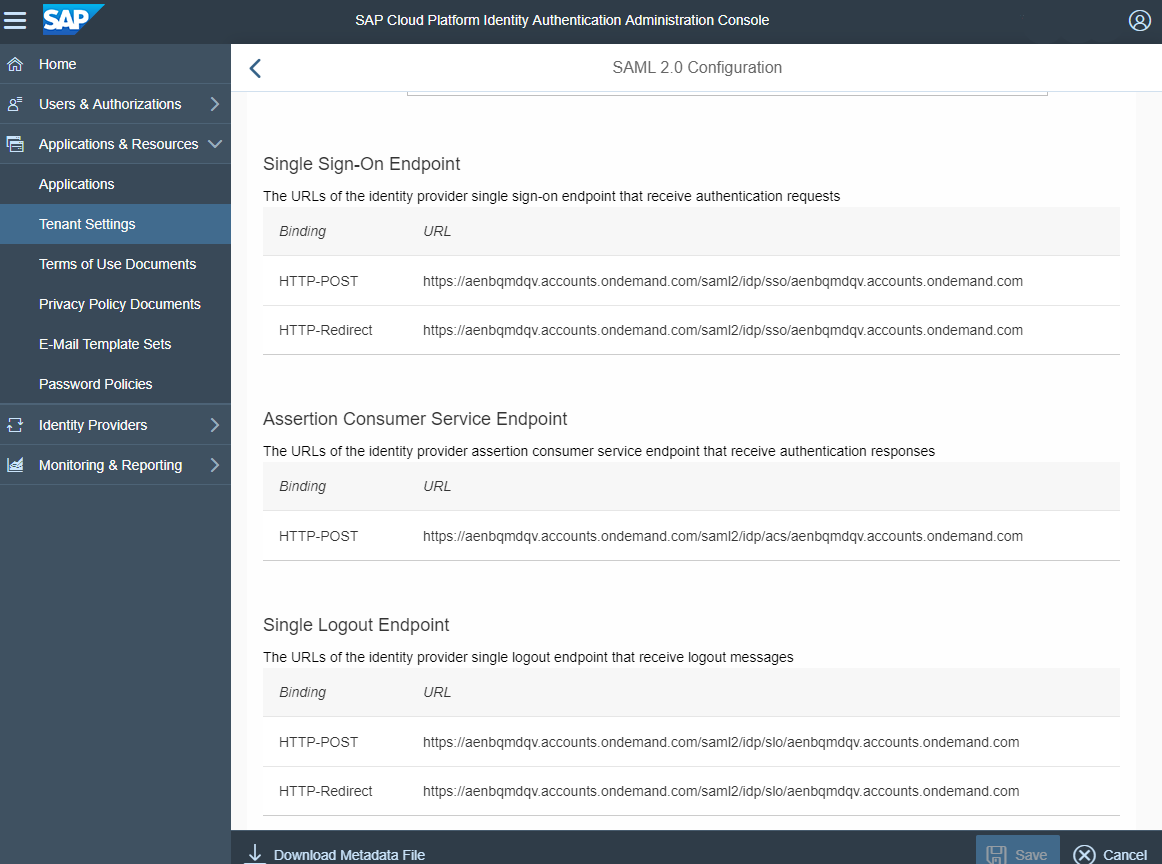
The Identity Provider Entity ID is the Identity Provider used. (e.g.: https://aenbqmdqv.accounts.ondemand.com)
The Saml Endpoint Location to be configured in the GAM backend should be taken from the SAP configuration (Single Sign On Endpoint). Likewise, the Single Logout Endpoint value to be configured in the backend should be taken from the Single Logout Endpoint in SAP.
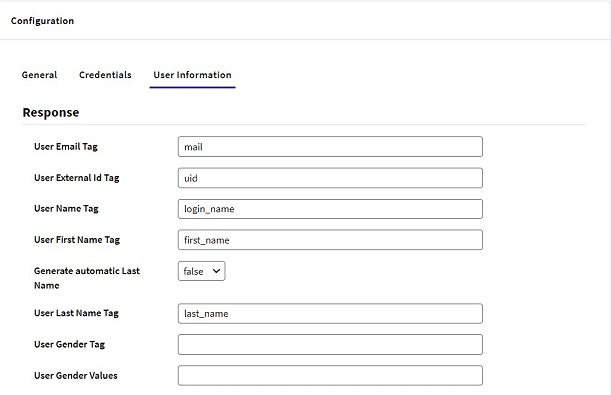
By default, SAP returns the following information: first name, last name, and email; all of which will be added to the assertion. It should be mapped in the SAML 2.0 Authentication type configuration under the User Information tab, as follows:
- User First Name tag: first_name
- User Last Name tag: last_name
- User E-mail tag: mail
If desired, further information may be added. First go through the "Assertion Attributes" -> Add option in the SAP Cloud Platform and select the attribute you wish to add. Then specify the tag in the User Information tab configuration of the SAML 2.0 Authentication type.
HowTo: Generate certificates for authentication using SAML 2.0 GAM Authentication