Note: As of July 2023, Microsoft has changed the name of its Azure Active Directory product to Microsoft Entra ID.
This tutorial explains how to authenticate your users using the OpenID Connect protocol with Azure Active Directory and GAM.
You need to use OAuth 2.0 Authentication Type and do some settings on the Azure Active Directory (Azure AD) Admin Center and the GAM's backend.
1. Define and register an application. See this guide from Microsoft.
2. Get the app's Application Id, since you'll need it later on:
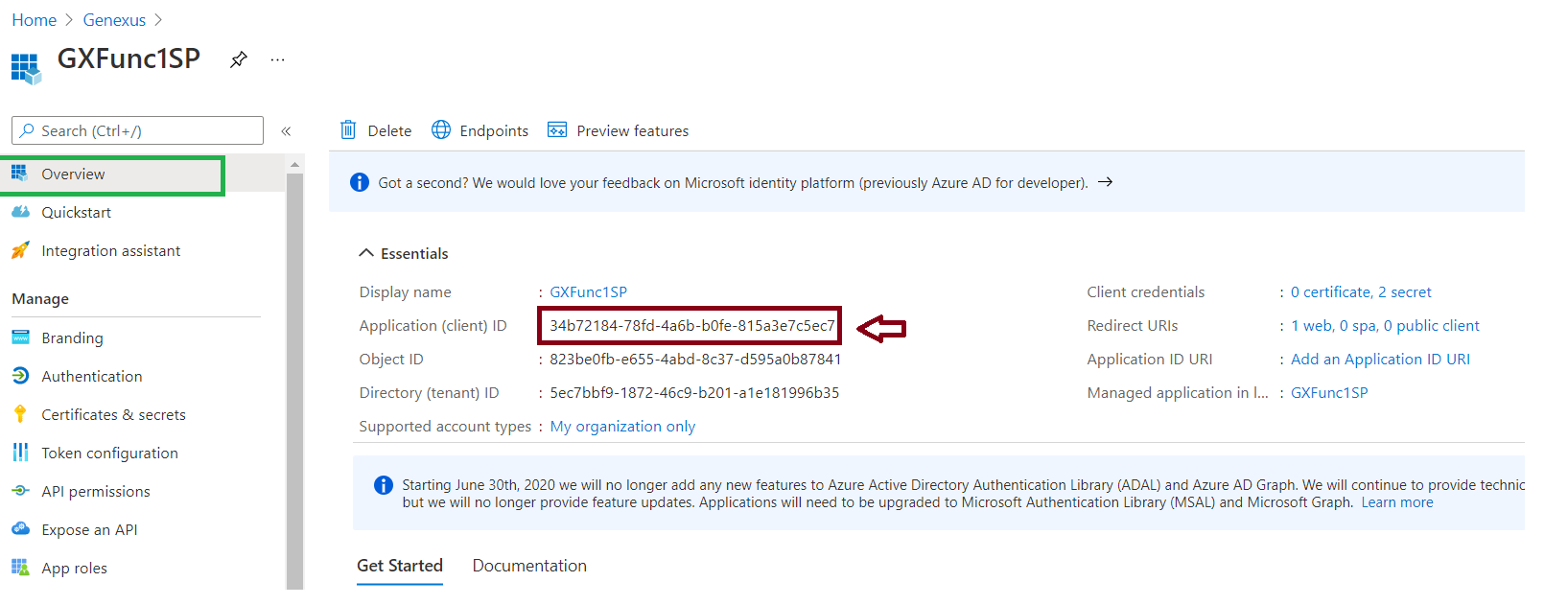
3. Configure a Redirect URI. Go through the Authentication menu option (Panel on the left) and create a new Web platform. Then add a Redirect URI of the form:
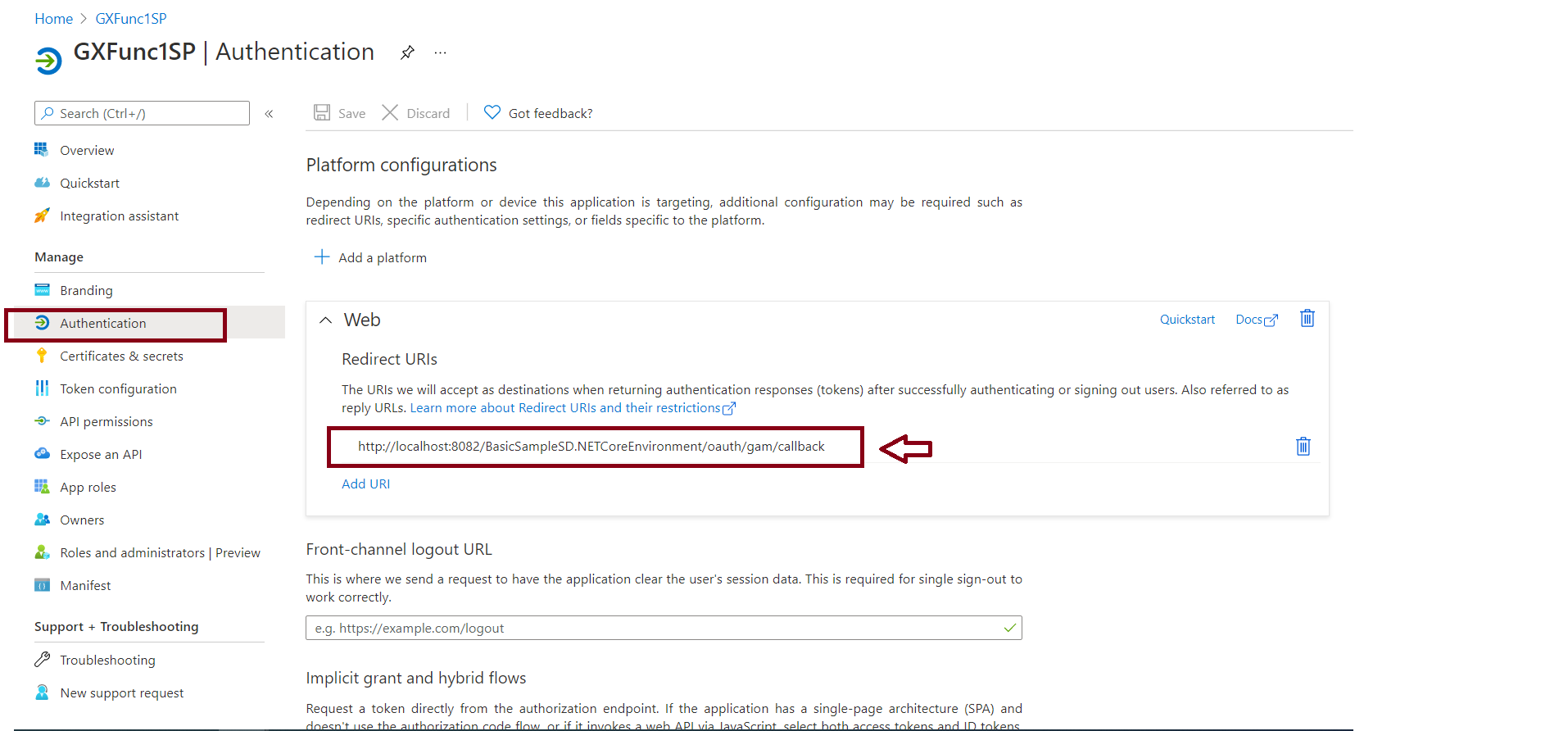
http://<server>:<port>/<BackendBaseURL>/oauth/gam/callback
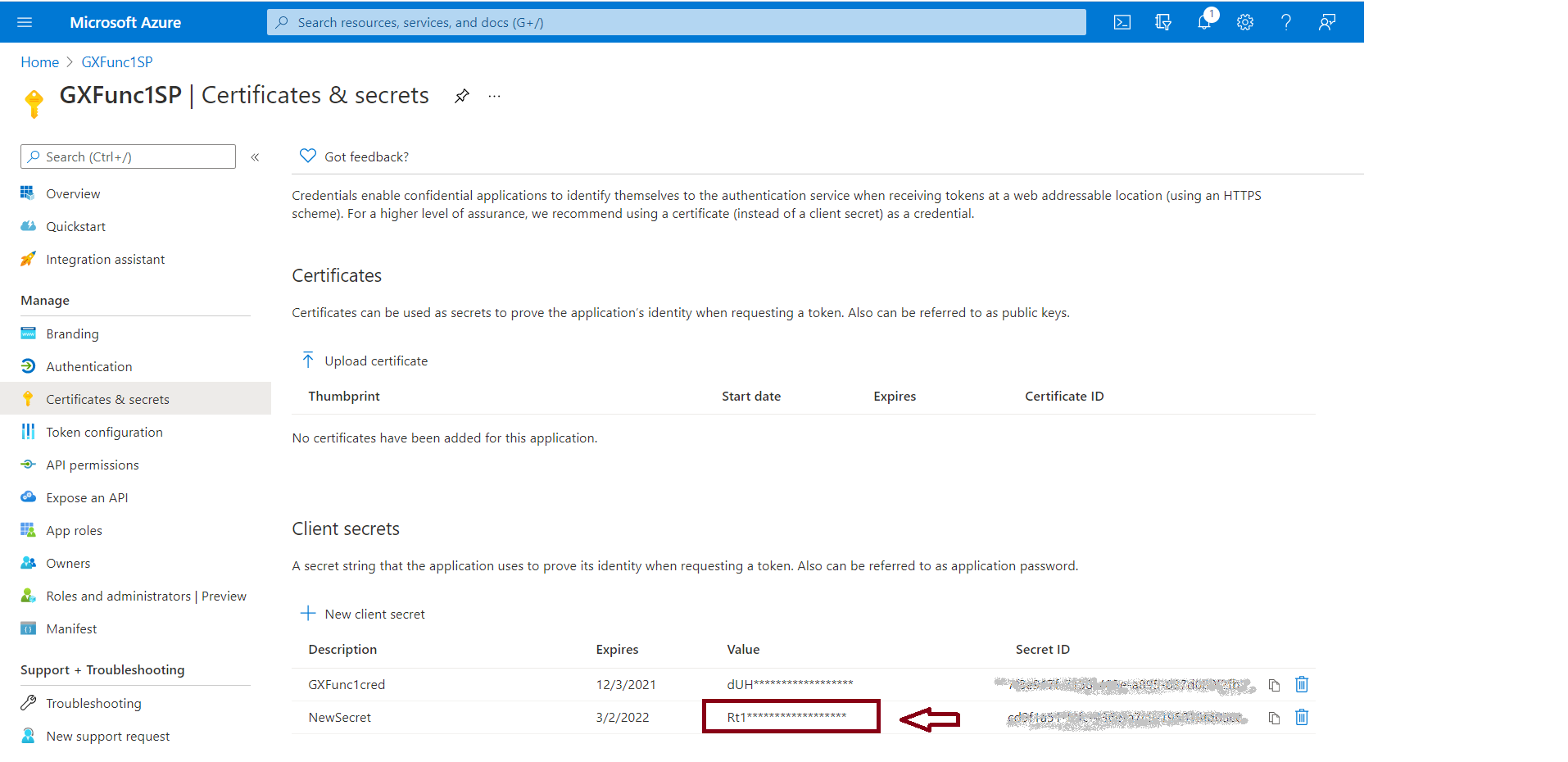
4. Go through the Certificates & secrets option, and create a NewSecret. You should copy the value of the secret, as it will be needed later.
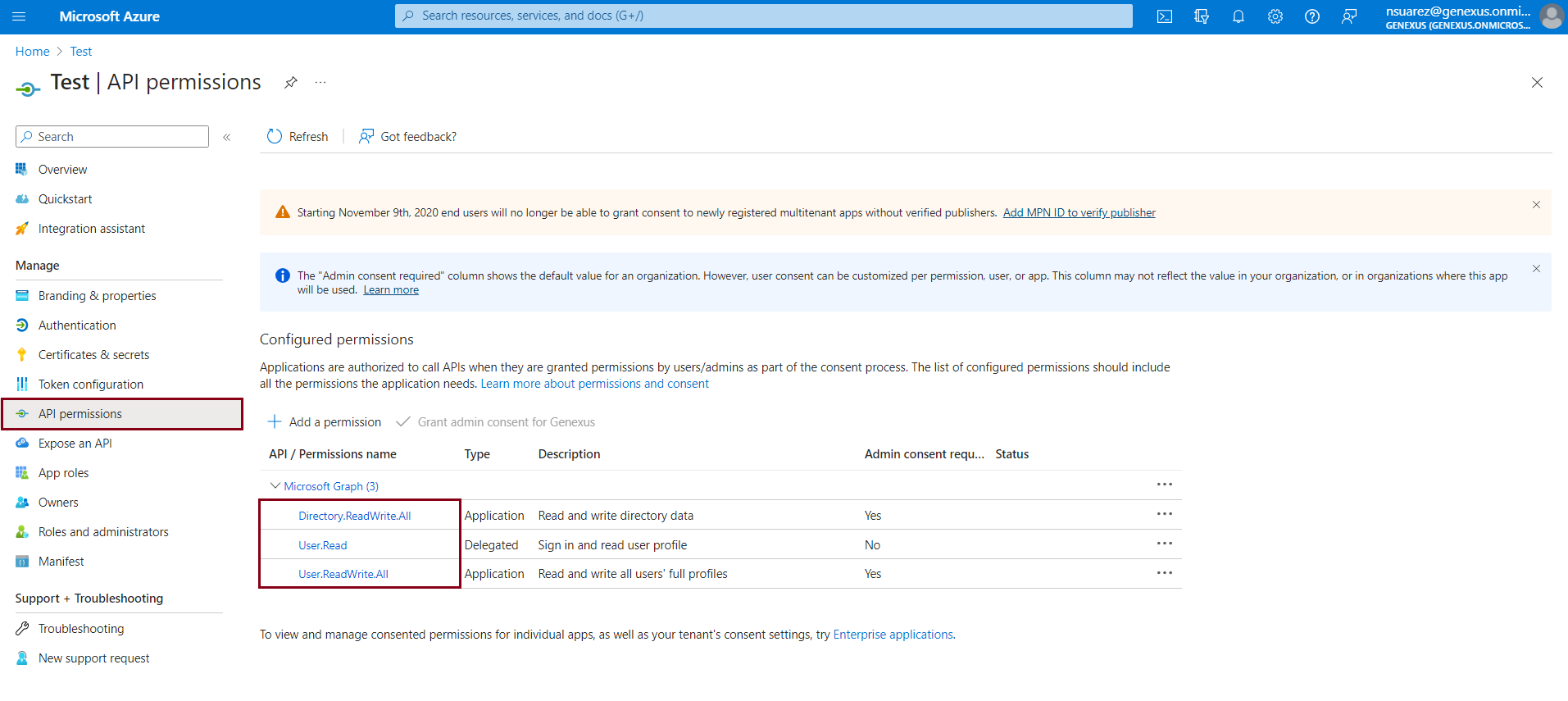
5. In the API permissions tab, verify that you have added the following:
The following steps will help you to obtain the certificate that you will later use in the GAM backend configuration.
6. From the endpoints panel, make a request to this URL: https://login.microsoftonline.com/organizations/v2.0/.well-known/openid-configuration in the browser or Postman:
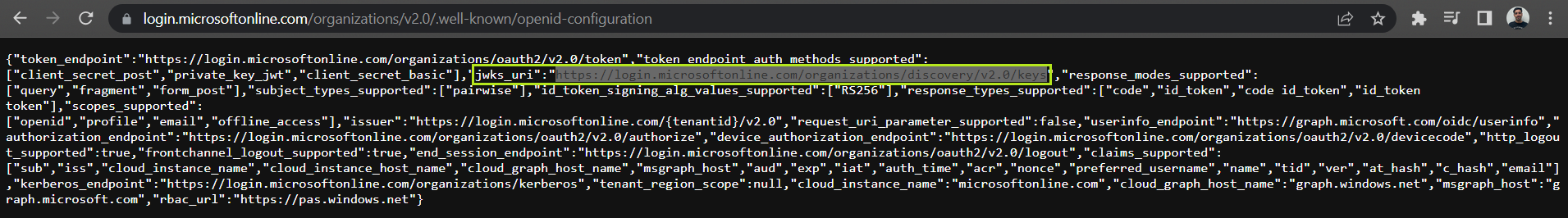
Take this URL and make a request in the browser or Postman.
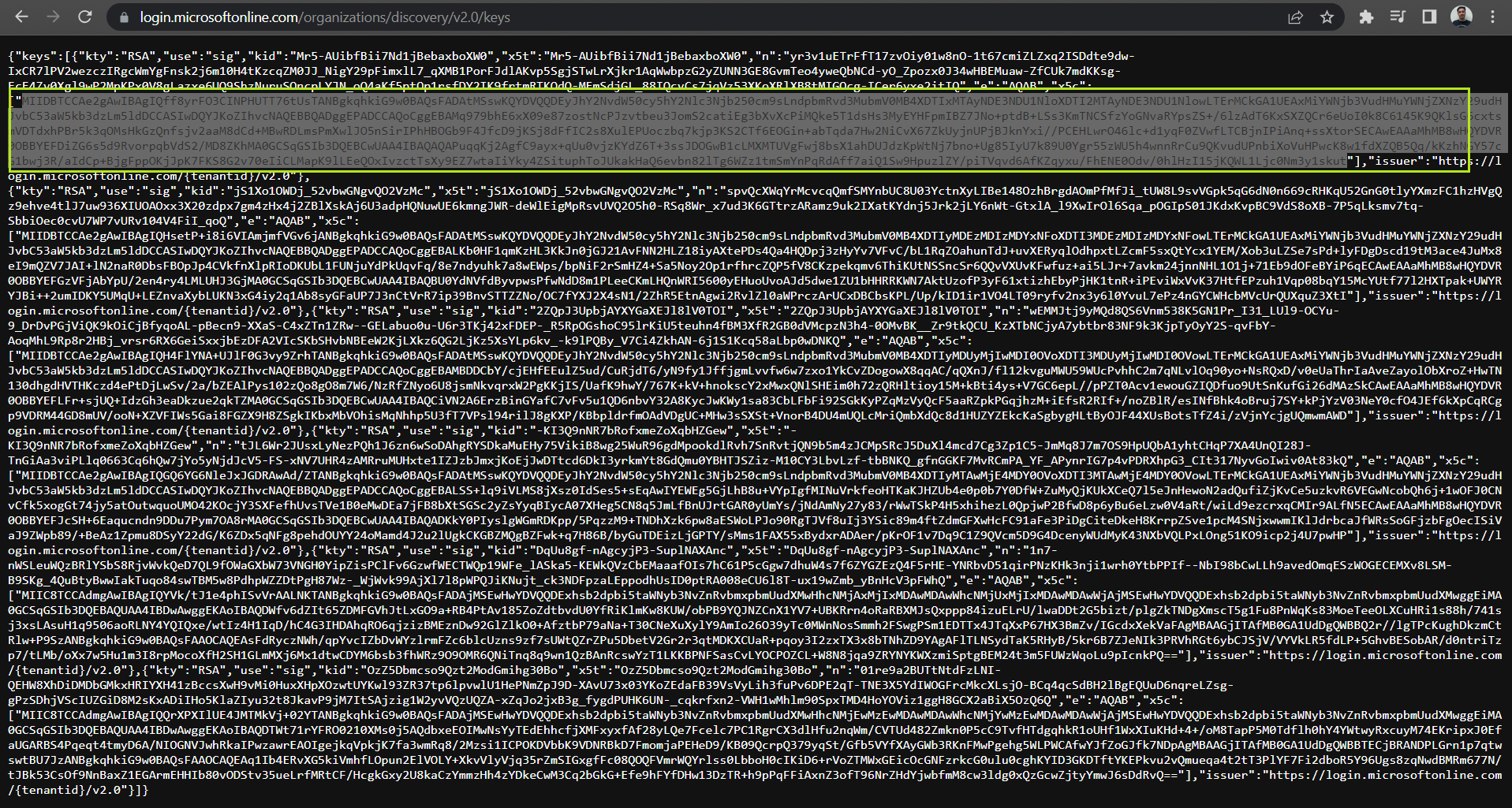
In this screen, Azure AD will give you six certificates and you can use any of them.
7. Go to Format Certificate Web Tool and paste the certificate you choose in the last step.
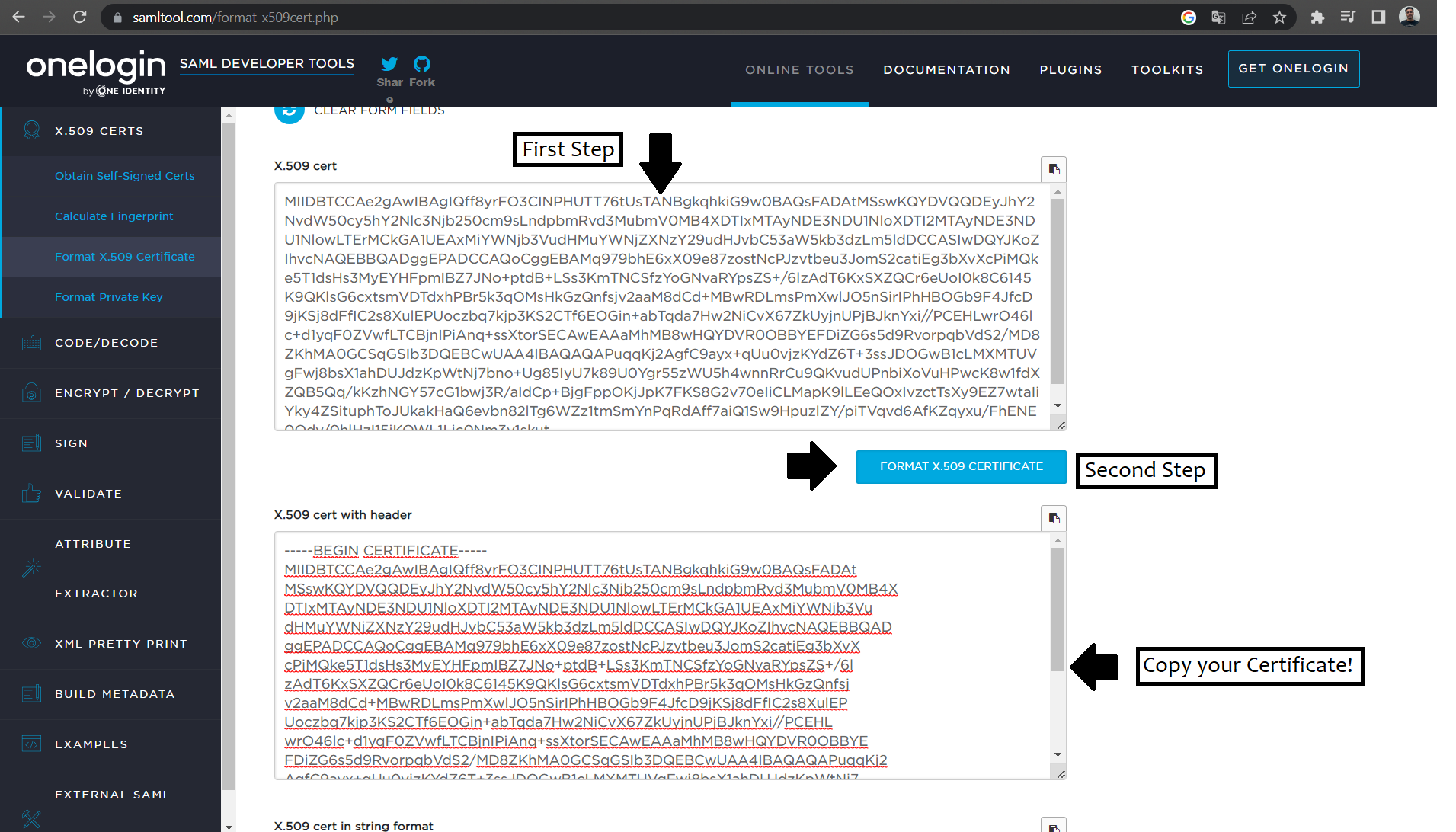
8. Create a .crt file in a folder (For example: C:/YourKB/NetSql/web/Certs), and paste the resulting certificate from the Certificate Web Tool.
9. Finally, upload this .crt certificate in the Upload certificate option:
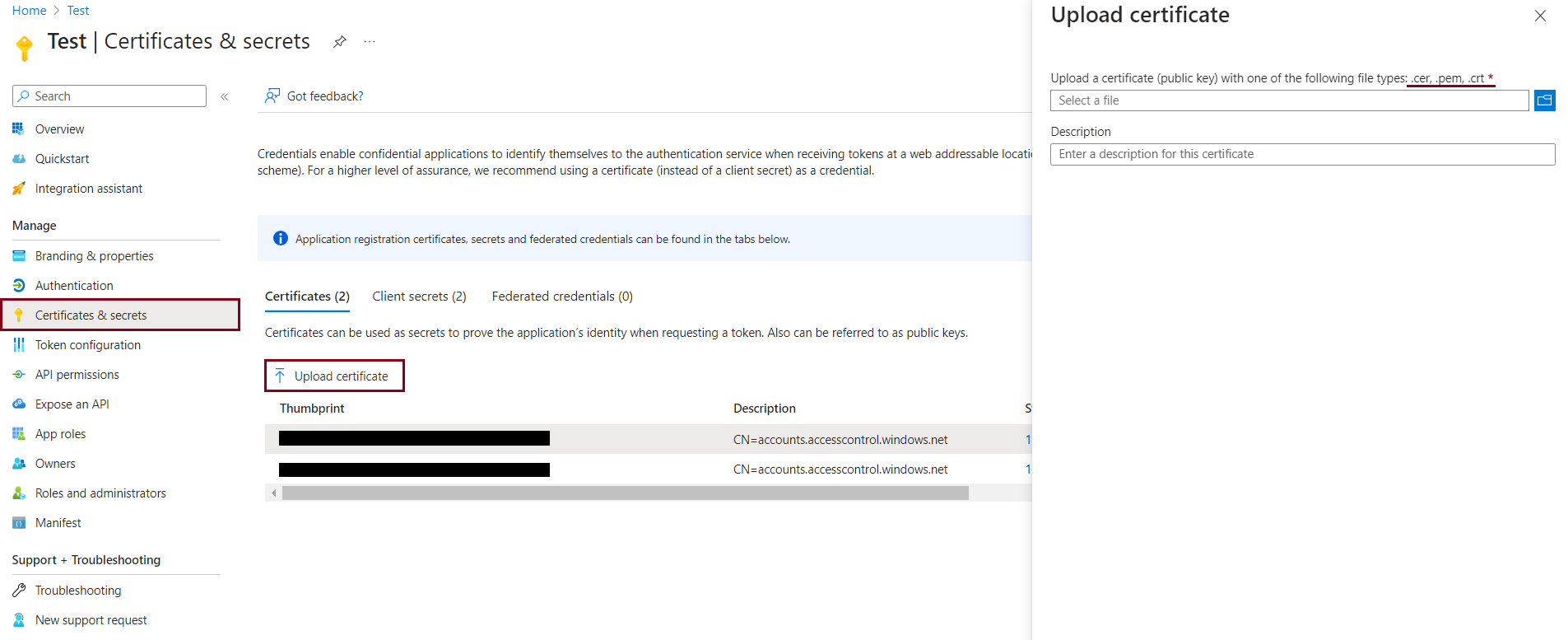
In the GAM Backend go to "Settings" and "Authentication Types" and create an OAuth 2.0 Authentication Type.
Go to the General tab and configure the following:
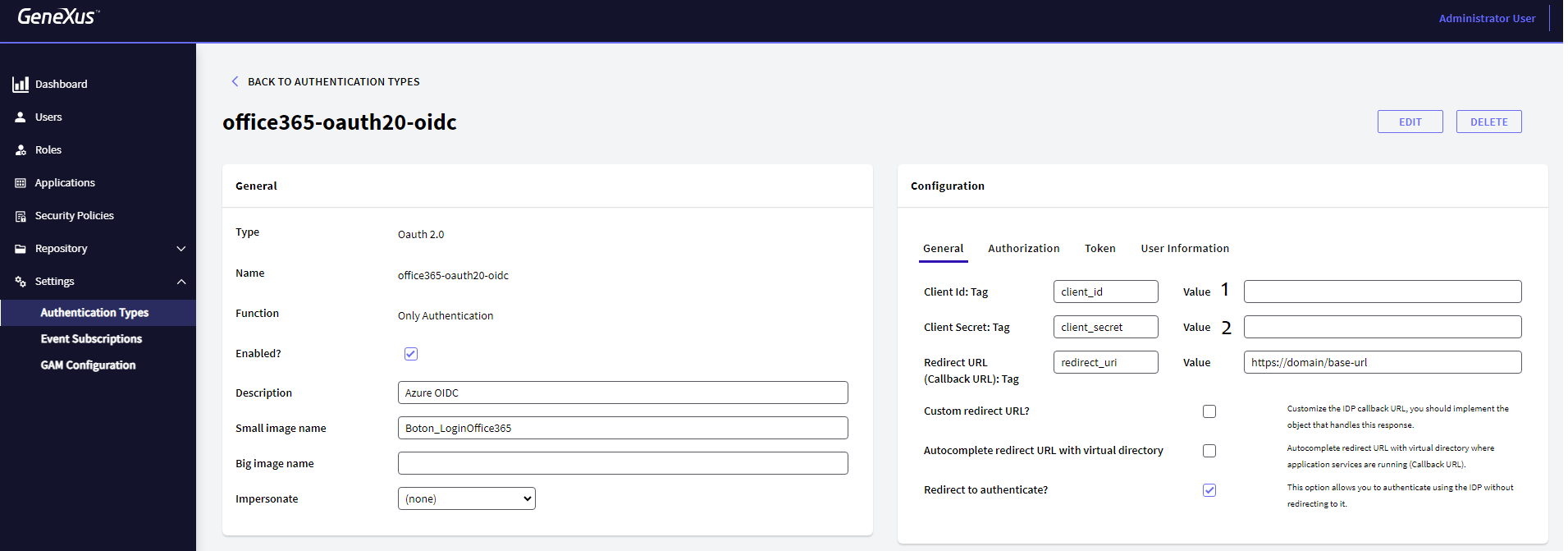
1. The Client Id value from the second step of the Azure AD portal configuration.
2. The Client Secret value from the fourth step of the Azure AD portal configuration.
Go to the Authorization Tab and configure the following:
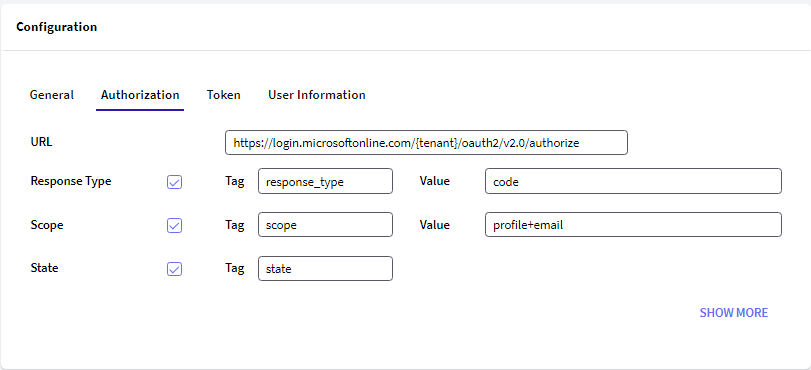
Note: The {tenant} value must be obtained from the application's Overview Panel.
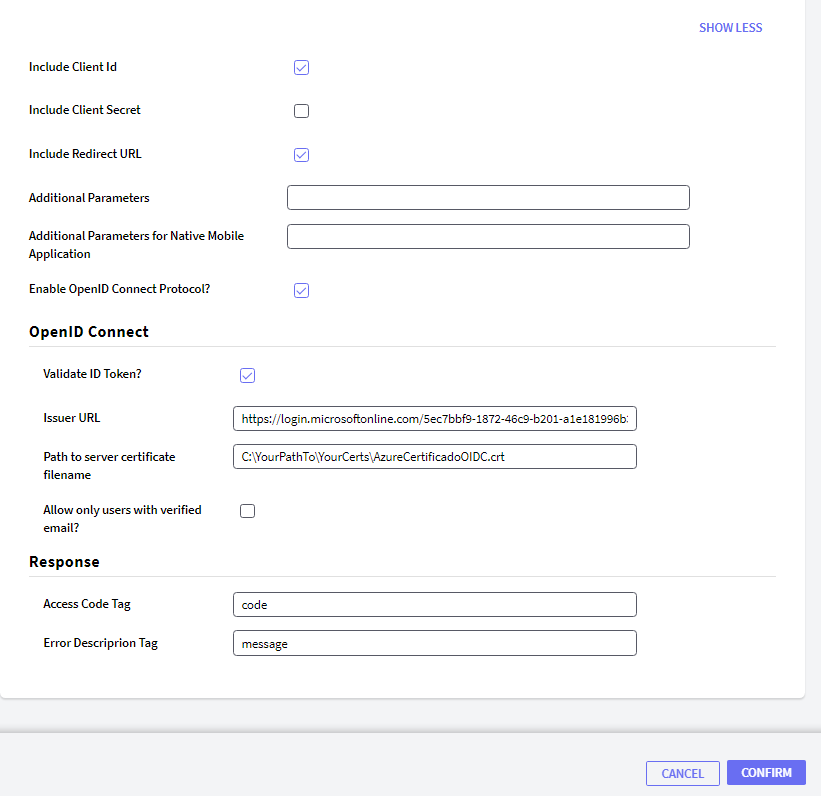
Important: For the OpenID connect authentication type to work correctly, make sure that you have checked "Enable OpenID Connect Protocol?" and "Validate ID Token".
Issuer URL: The value for this field must be obtained from the request to this URL: https://login.microsoftonline.com/organizations/v2.0/.well-known/openid-configuration in the browser or Postman.
Tip: To find the value in the request result, use Ctrl + F and type "issuer".
Go to Token Tab and configure the following:
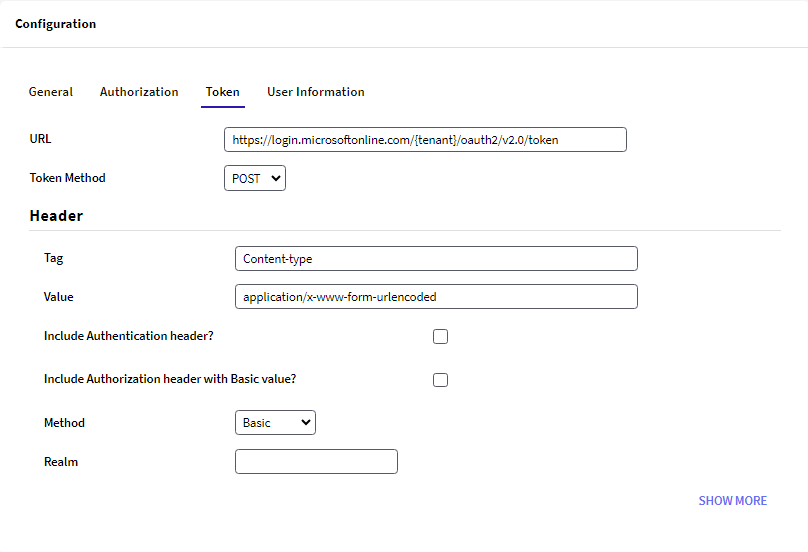
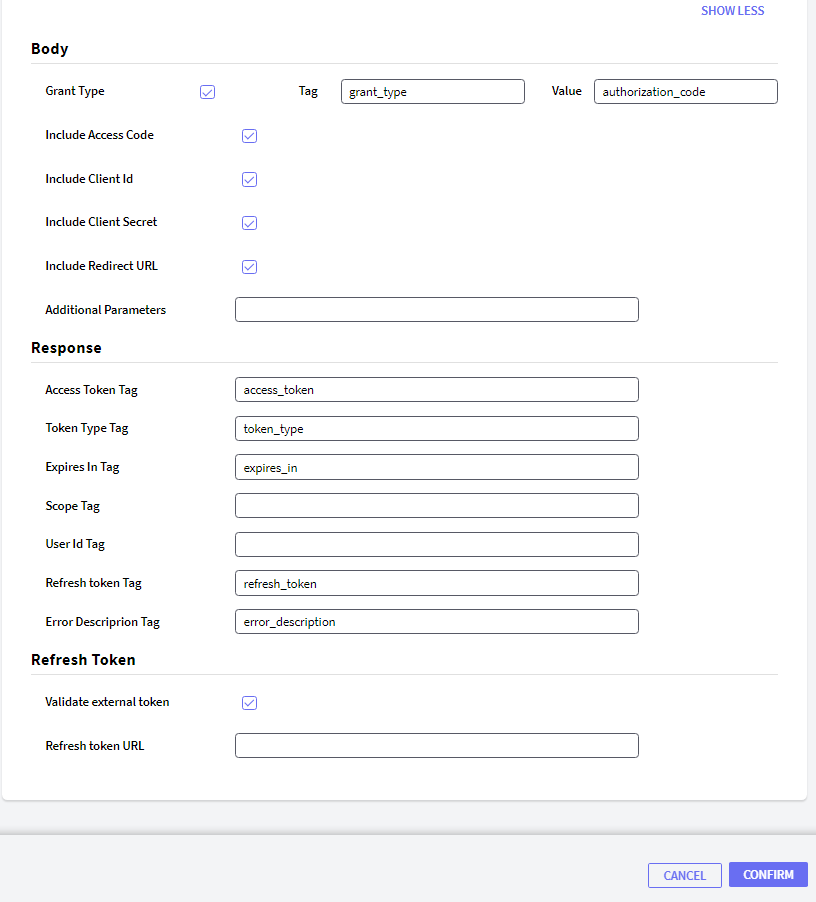
For the OpenID Connect authentication type, you do not have to configure anything in the user information tab.
GAM - OpenID Connect Authentication Type