In Remote REST Authentication type (OAuth 2.0), you should consider following some configuration steps at both the GAM of clients and at the Identity Provider's.
Note, here, the server-side configuration.
First define a GAM Application.
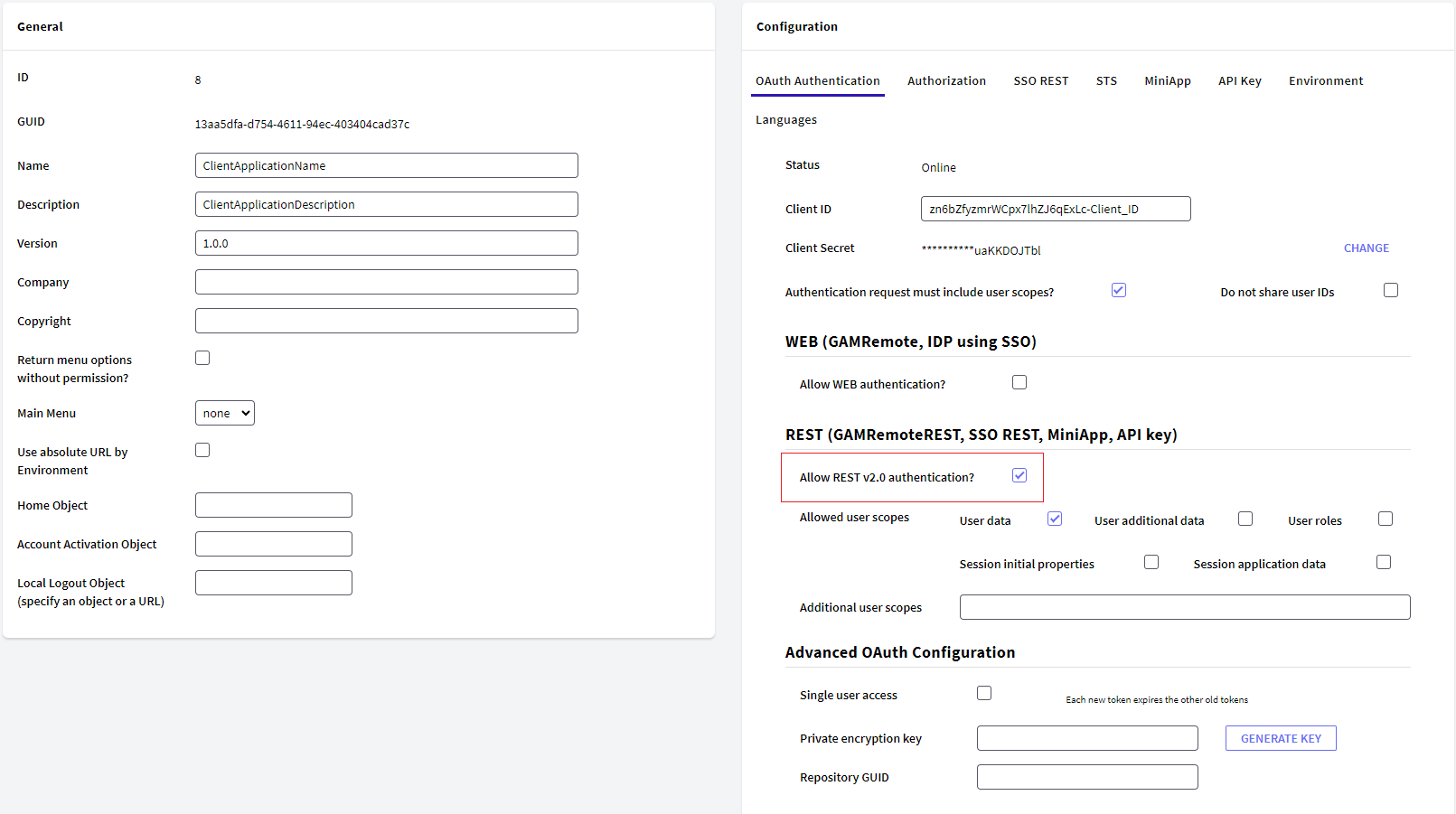
Note the Remote Authentication tab, set the Client Id and Client secret, which must match those configured at the client.
The configuration of the Application that applies to GAMRemoteREST authentication type is under section REST (GAMRemoteREST, SSO REST, MiniApp, API key).
-
Allow REST v2.0 authentication?. This must be checked to allow authentication to this GAM. When it is not checked, the following error is shown in the client upon an attempt to authenticate with the server: Remote authentication is not allowed in this application. Please contact the administrator. (GAM230)
-
Allowed user scopes. These scopes are the user data that the Client Application can access.The Client Application may request fewer scopes, but never more than those selected in this configuration. To know more details about them follow this link.
-
Additional user scopes. Here you can detail more specifically which user scopes to share with the Client Application. To know more details about them follow this link
-
Private encryption key. The call among RESTservices may be encrypted; the same key must be used for the Identity Provider (IDP) and for the client.
- RepositoryGUID. Specifies the repository GUID in the IDP. Only required when the IDP GAM is multitenant.
Client side configuration for GAMRemoteREST Authentication type